Certificate Inspector: Agent Deployment Strategies

Using a certificate management platform reduces the stress of obtaining SSL Certificates and managing existing ones. However, the tools that you use to manage your certificates are only as effective as you make them.
The Certificate Inspector platform from DigiCert includes an agent that you install on networks that you want to scan. Using the agent and the web-based portal you can scan your network and then analyze the overall health of your certificate landscape.
In one of our recent posts, we discussed port scanning recommendations. This post focuses on deployment strategies for your Certificate Inspector agents. There are many ways to deploy the agent on your network. Note that your individual needs will determine how you decide to deploy your agents. Below are the two most common agent deployment strategies.
Deployment Strategy #1
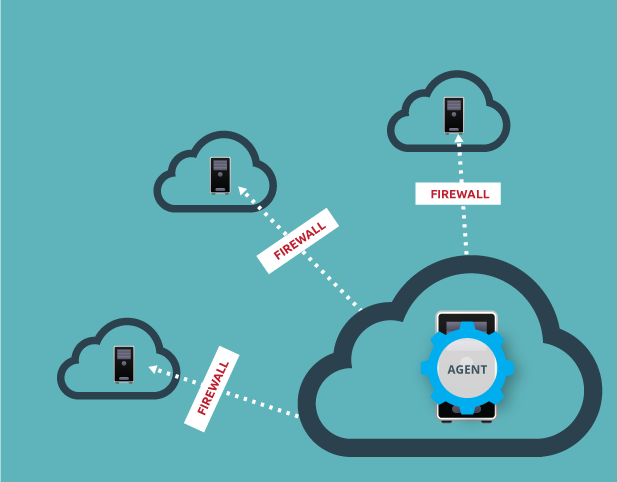
In this first strategy, the DigiCert Certificate Inspector Agent has been installed on one network. From that network, the agent performs scans on other networks and subnets. One advantage of this strategy is that all of the networks in your environment can be scanned with just one agent. A disadvantage with this strategy is that it requires you to configure an exception in each network's firewall so that the agent can scan it.
Deployment Strategy #2

In this strategy, an agent is deployed in each network and subnet. The advantage of this strategy is that there is no need to configure an exception in the firewalls for the agent to scan other networks and subnets, leading to stronger security. The disadvantage with this strategy is that it requires installing one agent per network and subnet, whereas the previous strategy can scan all connected networks at once.













