-
Solutions
Back
Digital Trust for:
Enterprise IT, PKI & Identity
Code & Software
Documents & Signing
IoT & Connected Devices
Manage PKI and Certificate risk in one place
Manage PKI and Certificate risk in one place
The smarter way to manage certificate lifecycles
Continuous Signing for CI/CD & DevOps
Secure, flexible and global signing
Trusted from silicon to in-the-field
Device security without compromise
Accelerate secure app development
Streamlined Certificate
Management and Automation:
Delivering At-Scale Uptime and Availability
2022 Edition of the TLS/SSL Best Practices Guide

2022 Edition of the TLS/SSL Best Practices Guide


How to establish a signing policy DevOps will actually adopt

Global perspective on managing document signing and regulations

Secure, update, monitor and control connected devices at scale

Secure, update, monitor and control connected devices at scale

Secure, update, monitor and control connected devices at scale

Secure, update, monitor and control connected devices at scale
DOWNLOAD NOW -
Buy
BackWildcard DomainBUY
Find the right TLS/SSL Certificate to secure your website
eIDAS-compliant transaction and website document security solutions
-
Insights
Back
Digital Trust for the Real World
Explore these pages to discover how DigiCert is helping organizations establish, manage and extend digital trust to solve real-world problems.
Ponemon Institute Report
See what our global post-quantum study uncovered about where the world stands in the race to prepare for quantum computing.
LEARN MORE >
-
Partners
Back
-
Support
Back
CONTACT OUR SUPPORT TEAM
- Americas
- 1.866.893.6565 (Toll-Free U.S. and Canada)
- 1.801.770.1701 (Sales)
- 1.801.701.9601 (Spanish)
- 1.800.579.2848 (Enterprise only)
- 1.801.769.0749 (Enterprise only)
- Europe, Middle East Africa
- +44.203.788.7741
- Asia Pacific, Japan
- 61.3.9674.5500
- Americas
- Contact us
- Language
- FAQ
- Code Signing Trust
- What is Code Signing?
Code Signing Trust
What is Code Signing?
-
-
Industry Standards for Security & Trust
What is Code Signing?
Code signing is the process of applying a digital signature to a software binary or file. This digital signature validates the identity of the software author or publisher and verifies that the file has not been altered or tampered with since it was signed. Code signing is an indicator to the software recipient that the code can be trusted, and it plays a pivotal role in combating malicious attempts to compromise systems or data.
Use cases for code signing include software for internal or external use, patches or fixes, testing, IoT device product development, computing environments, and mobile apps. Apart from code and software, code signing also applies to applications, firmware, files, messages, XML, scripts, containers, and images.
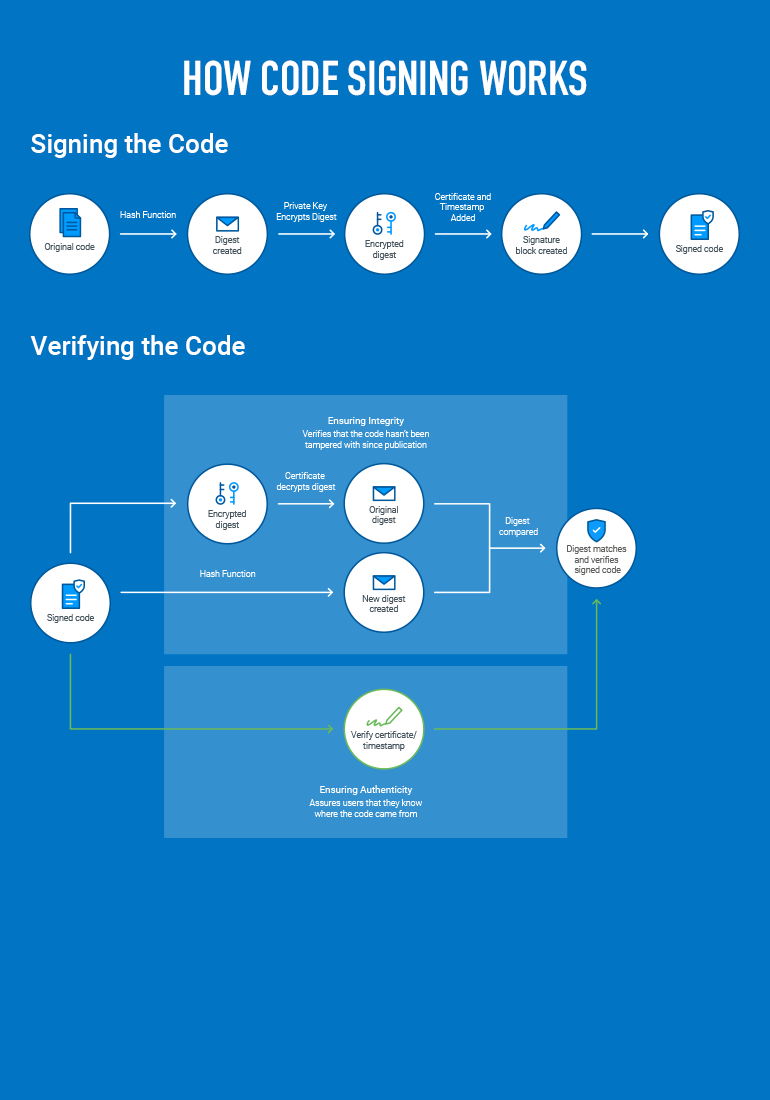
How Does Code Signing Work?
As with other PKI technologies, code signing involves a public/private key pair, a Certificate Authority and a digital certificate. When a publisher signs software, they create a bounded package that includes the publisher’s software, a code signing certificate and a digital signature. The code signing certificate contains the identity and public key of the publisher as well as the CA’s signature confirming that the CA has verified the identity. The digital signature is the signed hash of the software using the publisher’s private key. When the software is delivered, the user agent will check the certificate for validity and integrity (determining whether the software has been altered since signing). It uses the public key in the certificate to reveal the hash in the digital signature. It then compares the digital signature hash to the recently calculated hash from the software. If the hashes match, the customer or user is assured that the software has not been tampered with. Private key management is a critical security element in code signing. If the key is stolen or mismanaged, cybercriminals can use the key to sign malicious code and deliver it as updates to developer or customer systems.
Why do we Need to Code Sign?
Code signing is required by major software platforms such as Java and Microsoft to prevent malware propagation. It is also security best practice to sign code so that customers or users do not download tampered code or code from unknown sources. It distinguishes code or software from your organization versus code that may be packaged to look like it originated from your organization. Furthermore, when the software is made publicly available, users may encounter security warning labels when the software is not signed. When code is built and developed for internal use, code signing facilitates accountability and control.
What Types of Software can you Sign?
Any type of binary or file can be signed, including:
• Software applications made available for download from websites
• Internal IT applications
• Mobile applications
• XML files
• Scripts
• Software images
• Containers
• Drivers and utilities
• Firmware
What are the Steps Involved in Code Signing?
First, a software publisher generates a public/private key pair. Then they obtain a code signing certificate by submitting a Certificate Signing Request (CSR) along with their public key to a Certificate Authority (CA). The CA verifies the identity of the publisher and authenticates the certificate request. If successful, the CA issues the code signing certificate. The certificate includes the identity of the publisher, the public key and the signature of the CA. The signature of the CA is important, as it acts as a trusted third-party testimonial to the identity of the certificate bearer. The code signing certificate confirms not only the identity of the publisher, but also the integrity of the software. When the publisher signs software, they create a bounded package that includes the software, the code signing certificate and a digital signature.
The digital signature also requires the following steps:
- Generate a hash or cryptographically unique representation of the software with a hashing algorithm.
- Sign the hash with the publisher’s private key and a signing algorithm.
Code signing can be performed manually or automated as part of a software development lifecycle such as a Continuous Integration/Continuous Delivery (CI/CD) process.
-
Company
-
My Account
-
Resources
-
Solutions
-
© 2024 DigiCert, Inc. All rights reserved.
Legal Repository Audits & Certifications Terms of Use Privacy Center Accessibility Cookie Settings



