
Knowledge Base
Microsoft AD FS (IIS 8) | Create a CSR and Install SSL Certificate
These instructions are for Microsoft Active Directory Federation Services 2.0 on a Windows Server 2012/2012 R2.
Microsoft Active Directory Federation Services (AD FS) doesn’t include an easy GUI for creating a certificate signing request (CSR) and installing your SSL Certificate. Because Microsoft Active Directory Federation Services (AD FS) is designed to run on Microsoft IIS, you can use IIS 8/8.5 to create your CSR, and install your SSL Certificate in the Personal Store.
Next, use Microsoft Management Console (MMVC) to export the SSL Certificate as a .pfx and then import the SSL Certificate .pfx file in to the AD FS Personal Store. Finally, use the AD FS Management Console to assign the SSL Certificate to the AD FS service.
Use the instructions on this page to create your certificate signing request (CSR) and then to install your SSL Certificate.
To create your CSR, see Microsoft AD FS: Using IIS to Create Your CSR (Certificate Signing Request).
To install your SSL Certificate, see Microsoft AD FS: Using IIS, MMC, and AD FS to Install Your SSL Certificate.
For a simple way to create a CSR and install your SSL Certificate that works on any Microsoft server platform, you can use the DigiCert® Certificate Utility for Windows. See Microsoft AD FS: Create CSR and Install SSL Certificate (DigiCert Utility). For more information about this utility, see DigiCert® Certificate Utility for Windows.
Microsoft AD FS: Using IIS to Create Your CSR (Certificate Signing Request)
Microsoft Active Directory Federation Services (AD FS) doesn’t include a GUI for creating a CSR. Because AD FS is designed to run on Microsoft IIS, you can use IIS 8/8.5 to create your CSR.
AD FS: How to Create a CSR Using IIS 8/8.5
These instructions are for Microsoft Active Directory Federation Services 2.0 on a Windows Server 2012/2012 R2.
On your Windows 2012/2012R2 AD FS server, open Internet Information Services (IIS) Manager.
From the Windows Start screen, type and click Internet Information Services (IIS) Manager.
In Internet Information Services (IIS) Manager, under Connections, select your server’s Hostname.
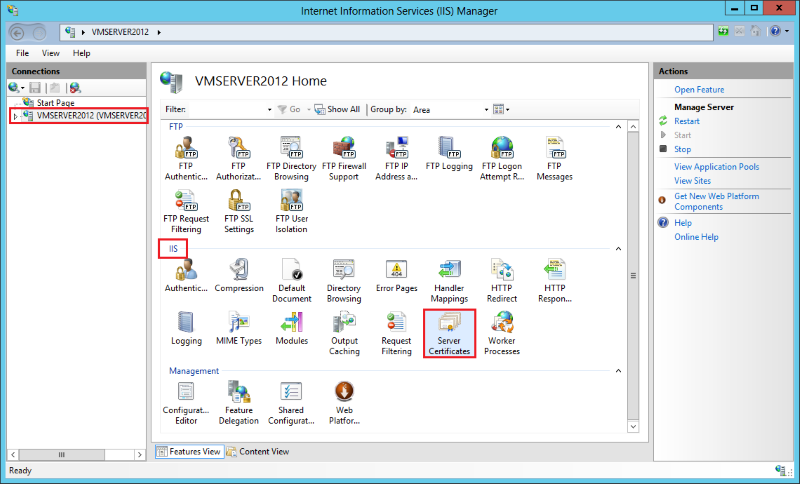
In the center menu, in the IIS section, double-click the Server Certificates icon.
In the Actions menu, click Create Certificate Request to open the Request Certificate wizard.
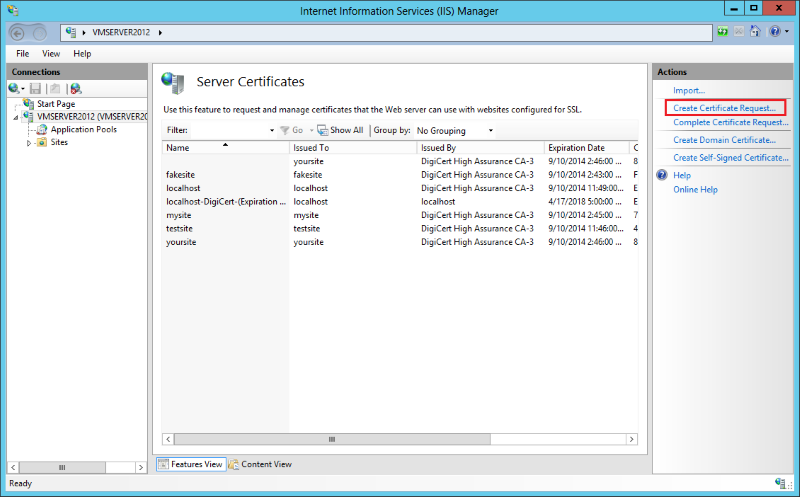
In the Request Certificate wizard, on the Distinguished Name Properties page, enter the following information and then, click Next:
Common name: Enter the name to be used to access the certificate. Make sure that the common name matches the name that clients will use to access the AD FS protected website.
Organization: Enter the legally registered name of your organization/company.
Organizational Unit: Enter the name of your department within the organization. For example, you can enter IT or Web Security. You can also leave the text box blank.
City/Locality: Enter the city in which your organiztaion/company is located.
State/Province: Enter the state/province in which your organiztaion/company is located.
Country/Region: Type or select your two-digit country code from the drop-down list. If necessary, you can find your two-digit country code in our SSL Certificate Country Codes list.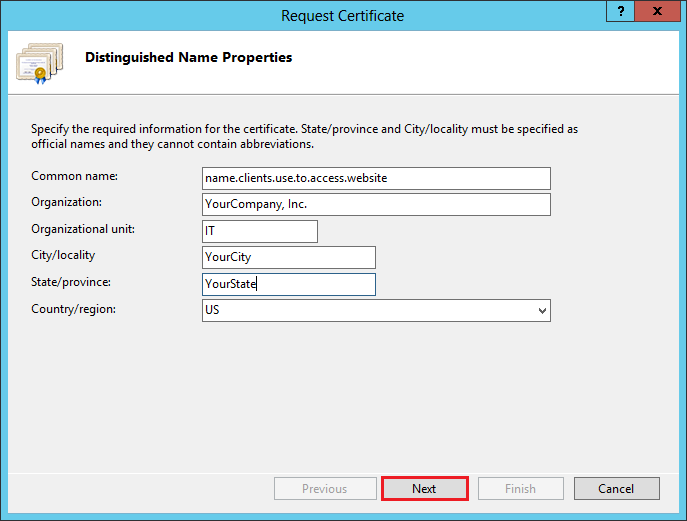
On the Cryptographic Service Provider Properties page, enter the following information and then, click Next:
Cryptographic service provider: In the drop-down list, select Microsoft RSA SChannel Cryptographic Provider, unless you have a specific cryptographic provider.
Bit length: In the drop-down list, select 2048.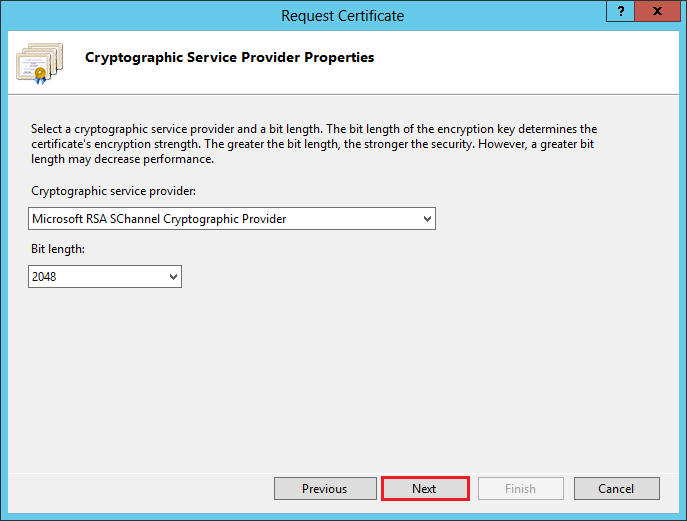
On the File Name page, click … to browse to a location where you want to save the CSR file, enter the filename, and then, click Open. Make sure to note the filename and the location where you saved your CSR file.
Note: If you only enter the filename without selecting a location, your CSR file is saved to the following location: C:\Windows\System32.
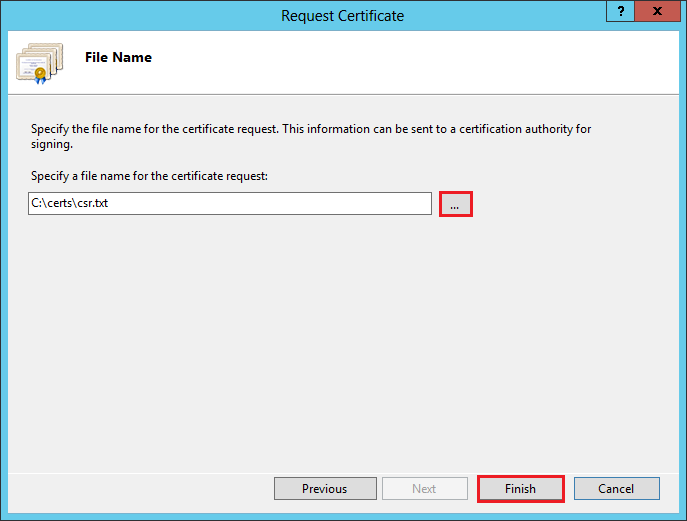
Click Finish.
Open the file in a text editor. Then, copy the text, including the—-—- BEGIN NEW CERTIFICATE REQUEST----- and—-—-END NEW CERTIFICATE REQUEST----- tags, and paste it into the DigiCert order form.
Note: During your DigiCert SSL Certificate ordering process, make sure that you select Microsoft IIS 8 when asked to Select Server Software. This option ensures that you receive all the required certificates for Microsoft Active Directory Federation Services SSL Certificate installation (Intermediate and SSL Certificates).
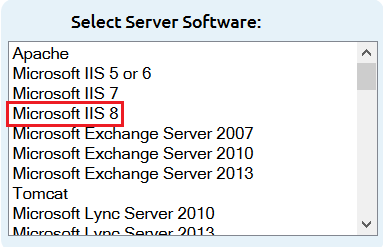
After you receive your SSL Certificate from DigiCert, you can install it.
Microsoft AD FS: Using IIS, MMC, and AD FS to Install Your SSL Certificate
If you have not yet created a Certificate Signing Request (CSR) and ordered your certificate, see Microsoft AD FS: Using IIS to Create Your CSR (Certificate Signing Request).
These instructions are for Microsoft Active Directory Federation Services 2.0 on a Windows Server 2012/2012 R2.
Microsoft AD FS: How to Install Your SSL Certificate
The installation process consists of the following steps:
Use IIS to install the certificate on your Winodws Server 2012 AD FS server.
Using IIS 8/8.5 to Install the SSL Certificate on Your AD FS Server.
Use Microsoft Management Console (MMC) to export the certificate as a .pfx file.
Use the MMC to import the SSL Certificate .pfx file in to the AD FS Personal Store.
Using the MMC to Import the SSL Certificate .pfx File in to the AD FS Personal Store.
Use the AD FS Console to assign the SSL Certificate to the AD FS service.
Using the AD FS Console to Assign the SSL Certificate to the AD FS Service
Use PowerShell to tell AD FS service to use the SSL Certificate.
i. Using IIS 8/8.5 to Install the SSL Certificate on Your AD FS Server
After DigiCert validates and issues your SSL Certificate, you can use IIS to install your SSL Certificate on the server where you generated the CSR.
On your Windows 2012/2012R2 AD FS server where you created the CSR, open the ZIP file containing your SSL Certificate and save the SSL Certificate file (i.e. your_domain_name.cer) to the desktop.
Open Internet Information Services (IIS) Manager.
From the Windows Start screen, type and click Internet Information Services (IIS) Manager.
In Internet Information Services (IIS) Manager, under Connections, select your server’s Hostname.

In the center menu, in the IIS section, double-click the Server Certificates icon.
In the Actions menu, click Complete Certificate Request to open the Complete Request Certificate wizard.
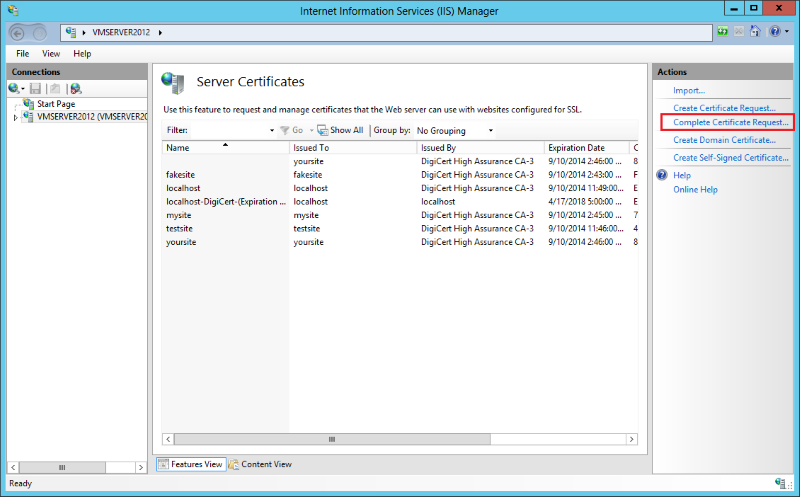
In the Complete Certificate Request wizard, on the Specify Certificate Authority Response page, under File name containing the certification authority’s response, click ... to browse to the .cer certificate file that DigiCert sent you, select the file, and then click Open.
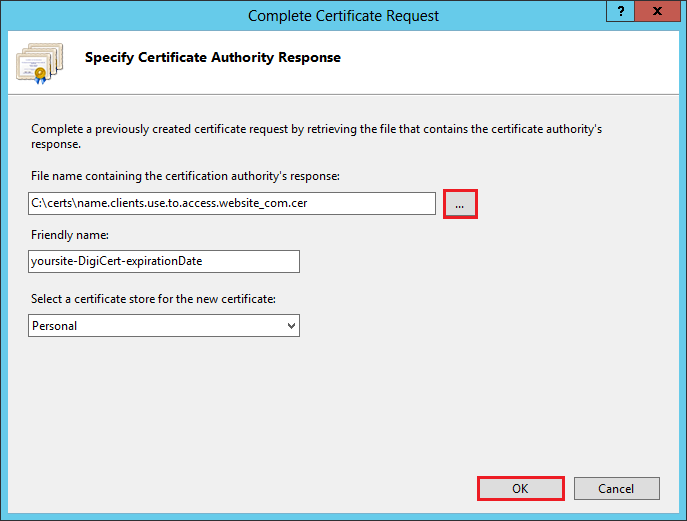
Next, in the Friendly name box, enter a friendly name for the certificate. The friendly name is not part of the certificate but is used to identify the certificate.
We recommend that you add DigiCert and the expiration date to the end of your friendly name, for example: yoursite-DigiCert-expirationDate. This information helps identify the issuer and expiration date for each certificate. It also helps distinguish multiple certificates with the same domain name.
Next, in the Select a certificate store for the new certificate drop-down list, select Personal.
To install the SSL Certificate on the server, click OK.
Now that you have successfully installed the SSL Certificate on the server, use the Microsoft Management Console (MMC) to export the certificate as a .pfx file.
ii. Using the MMC to Export the SSL Certificate as a .pfx File
On your Windows 2012/2012R2 AD FS server, open the Microsoft Management Console (MMC) as an admin.
From the Windows Start screen, type mmc.exe.
Right-click on mmc.exe.
In the menu at the bottom of the screen, click Run as administrator.
In the User Account Control window, click Yes to allow the program to make changes to the computer.
In the MMC Console, in the menu at the top of the page, click File > Add/Remove Snap-in.
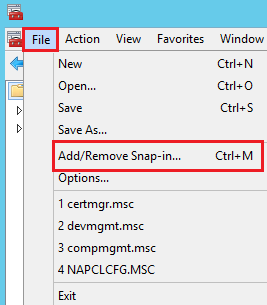
In the Add or Remove Snap-ins window, under Available snap-ins (left side), click Certificates and then, click Add.
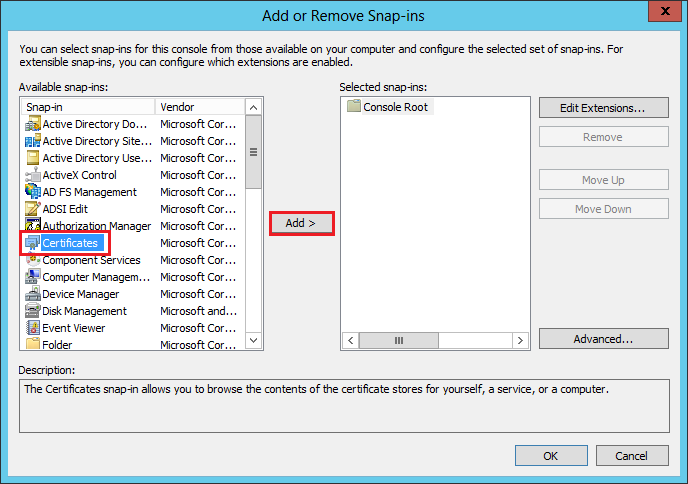
In the Certificates snap-in window, select Computer account and then, click Next.
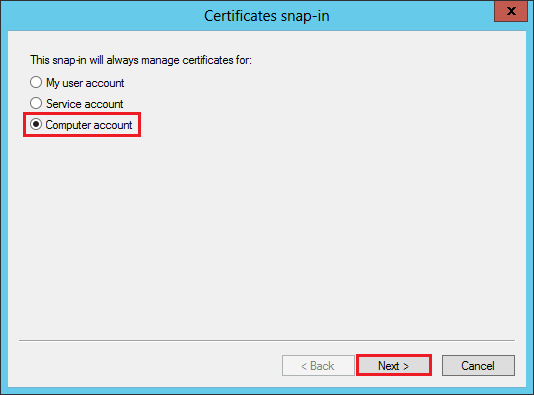
In the Select Computer window, select Local computer (the computer this console is running on), and then, click Finish.
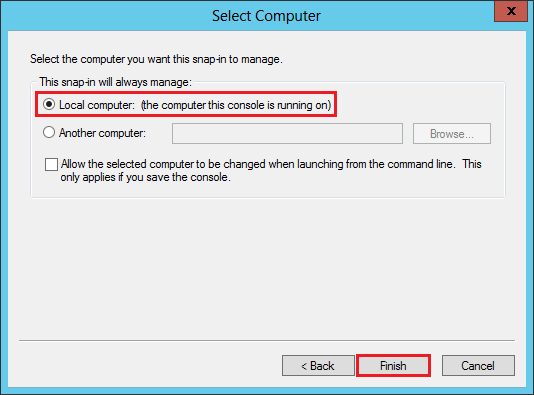
In the Add or Remove Snap-ins window, click OK.
In the MMC Console, in the console tree, expand Certificates (Local Computer) > Personal, and then, click Certificates.
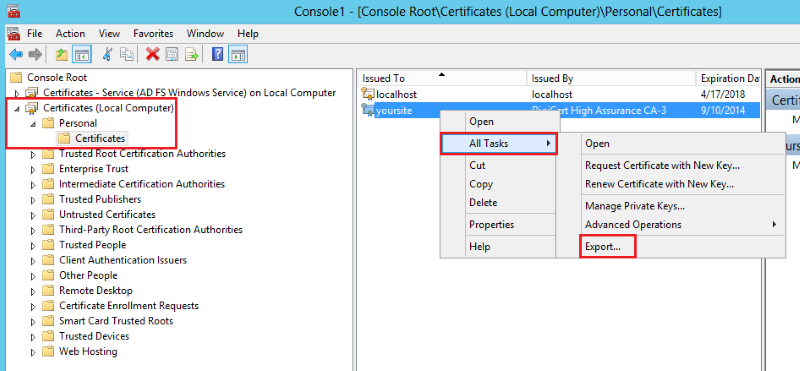
In the center section, right-click on your newly installed SSL Certificate and then, click All Tasks > Export to open the Certificate Export Wizard.
In the Certificate Export Wizard, on the Welcome to the Certificate Export Wizard page, click Next.
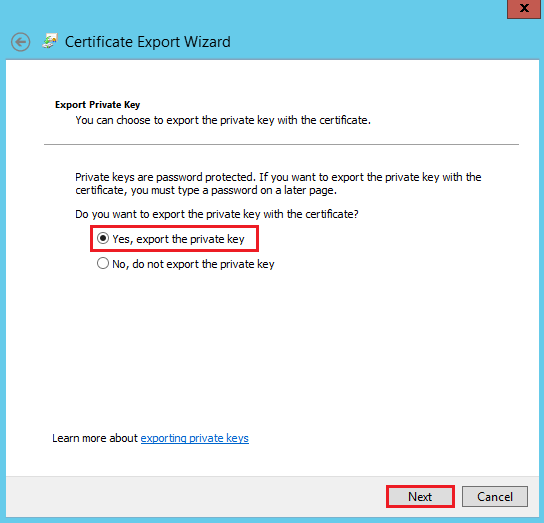
On the Export Private Key page, select Yes, export the private key, and then, click Next.
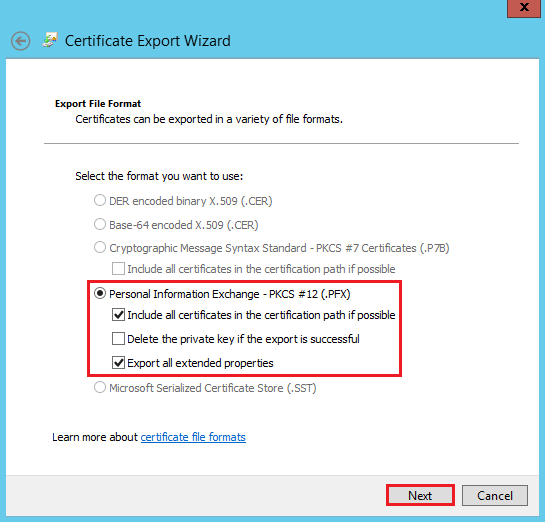
On the Export File Format page, select Personal Information Exchange - PKCS #12 (.PFX), check Include all certificates in the certification path if possible and Export all extended properties, and then, click Next.
Warning: Do not check Delete the private key if the export is successful.
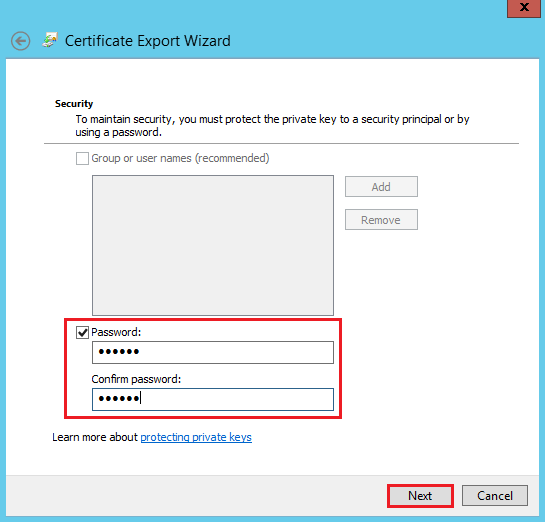
On the Security page, check Password, enter and confirm your password, and then, click Next.
On the File to Export page, click Browse and browse to and select where you want to save the certificate .pfx file, name the file, and then, click Save.
Make sure to note the filename and the location where you saved your file.
If you only enter the filename without selecting a location, your file is saved to the following location: C:\Windows\System32.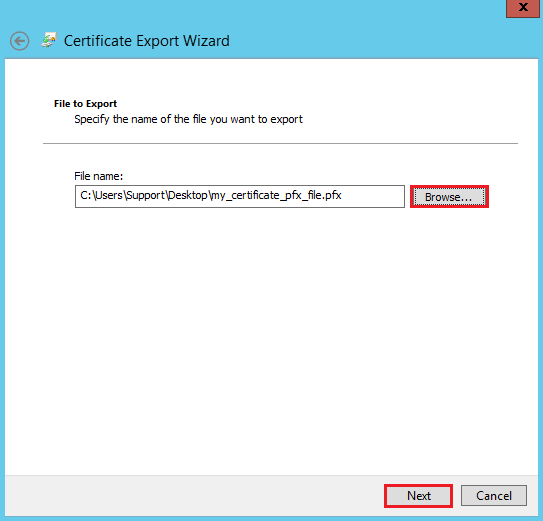
On the File to Export page, click Next.
On the Completing the Certificate Export Wizard page, verify that the settings are correct and then, click Finish.
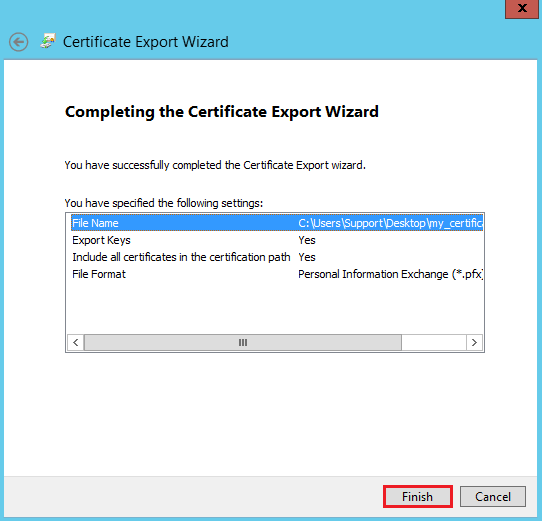
You should receive "The export was successful" message.
Now that you have successfully exported the SSL Certificate as a .pfx file, use the Microsoft Management Console (MMC) to import the SSL Certificate in to AD FS Personal Store.
iii. Using the MMC to Import the SSL Certificate .pfx File in to the AD FS Personal Store
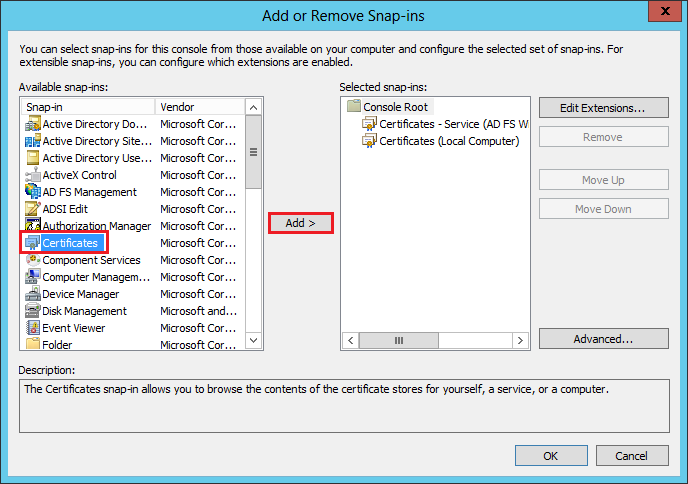
In the MMC Console, in the menu at the top, click File > Add/Remove Snap-in.

In the Add or Remove Snap-ins window, under Available snap-ins (left side), click Certificates and then, click Add.
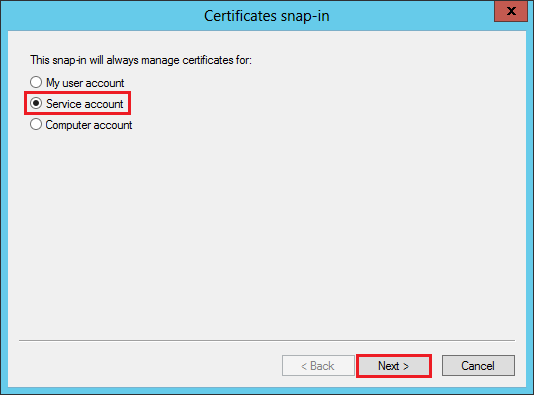
In the Certificates snap-in window, select Service account and then, click Next.
In the Select Computer window, select Local computer (the computer this console is running on), and then, click Next.
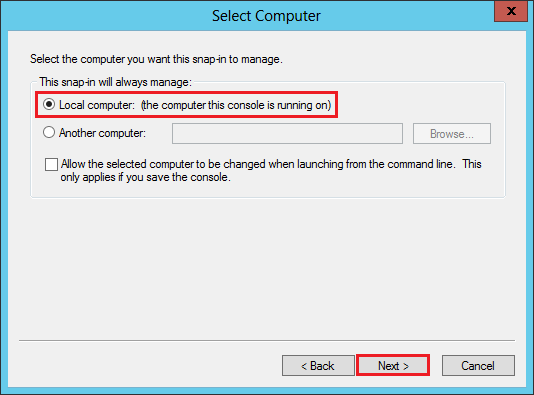
In the Certificate snap-in window, select AD FS Windows Service and then, click Finish.
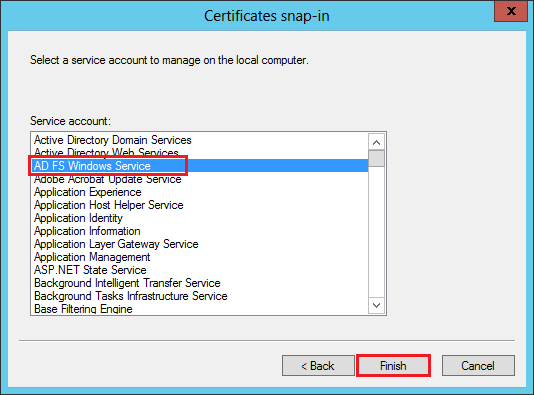
In the Add or Remove Snap-ins window, click OK.
In the MMC Console, in the console tree, expand Certificates - Service (AD FS Windows Service) > Personal, and then, click Certificates.
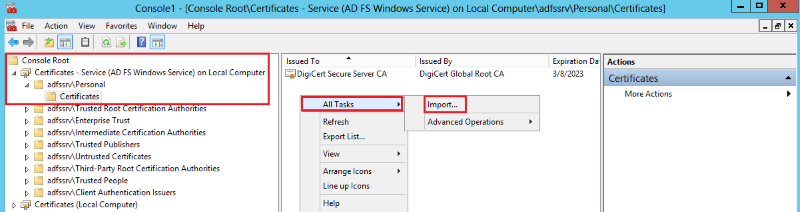
Right-click on the center section and then click All Tasks > Import to open the Certificate Import Wizard.
In the Certificate Import Wizard, on the Welcome to the Certificate Import Wizard page, click Next.
On the File to Import page, click Browse to browse to the SSL Certificate .pfx file that you exported earlier, select the file, and then, click Open.
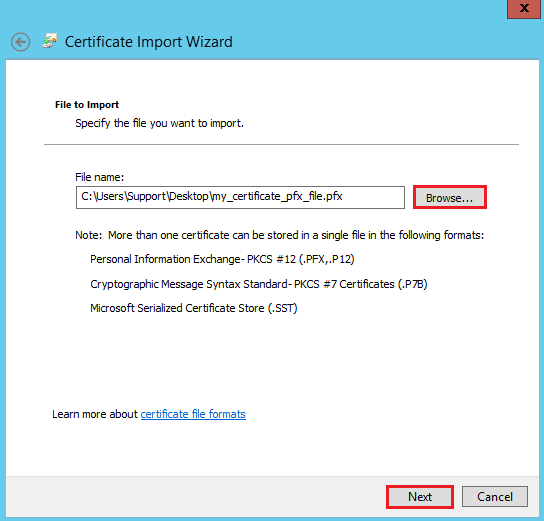
On the File to Import page, click Next.
On the Private key protection page, do the following thing and then, click Next:
- In the Password box, enter the password you created to export your SSL Certificate as a .pfx file.
- Check Mark this key as exportable.
- Check Include all extended properties.
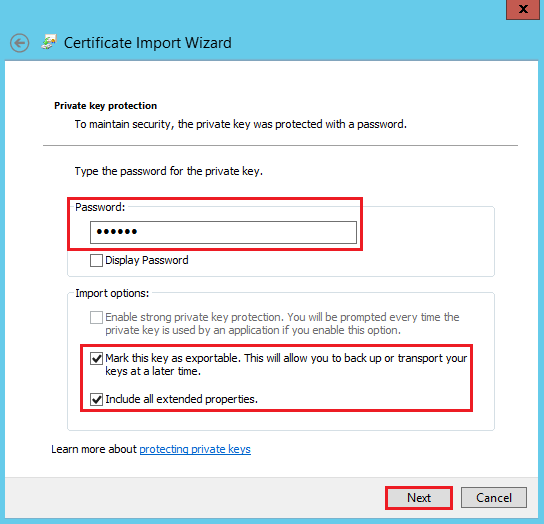
On the Certificate Store page, make sure that Place all certificates in the following store is selected and the Certificate store box is populated with the Personal store, and then, click Next:
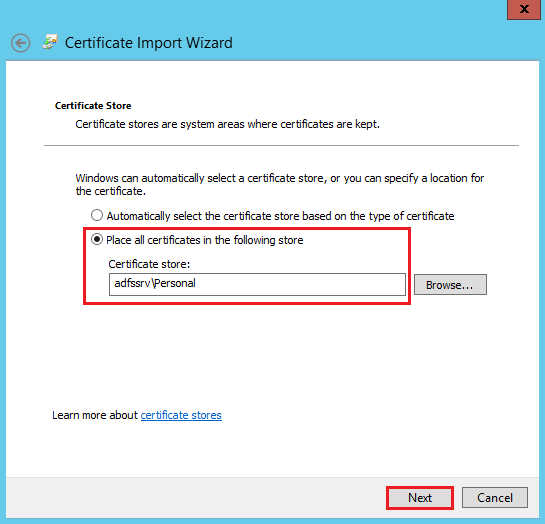
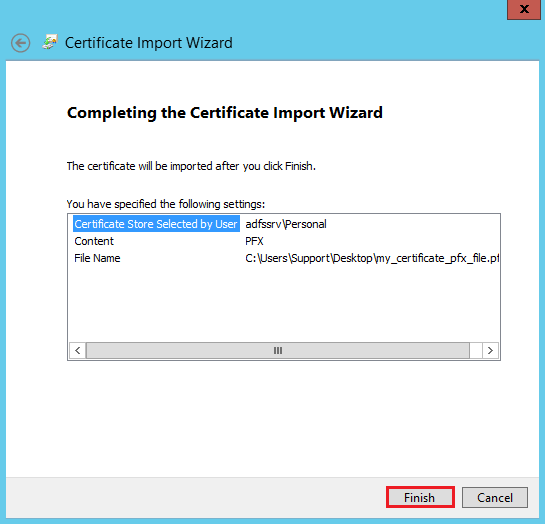
On the Completing the Certificate Import Wizard page, verify that the settings are correct and then, click Finish.
You should receive a "The import was successful" message.
Now that you have successfully imported the SSL Certificate .pfx file into the AD FS Personal Store, use the AD FS management console to assign the SSL Certificate to the AD FS service.
iv. Using the AD FS Management Console to Assign the SSL Certificate to the AD FS Service
On your Windows 2012/2012R2 AD FS server, open the AD FS management console as an admin.
From the Windows Start screen, type ad fs management.
Right-click on AD FS Management.
In the menu at the bottom of the screen, click Run as administrator.
In the User Account Control window, click Yes to allow the program to make changes to the computer.
In the AD FS Console window, in the console tree, expand Services, right-click on the Certificates folder, and select Set Service Communications Certificate.
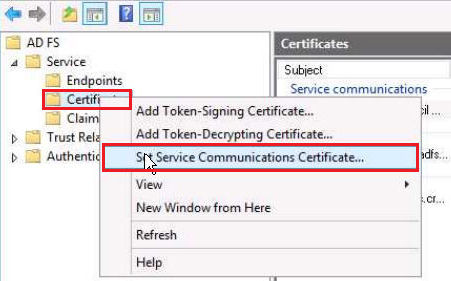
Now, in the Windows Security window, select the new SSL Certificate that you just imported in to the AD FS Personal Store in the previous section and then, click OK.
In the AD FS Management window, a private key warning reminds you that the selected certificate’s private key must be accessible.
This is a reminder that you need to ensure that the private key is correctly associated with your SSL Certificate during the installation process.
Click OK.
Your SSL Certificate should be successfully assigned to the AD FS Service.
v. Using PowerShell to Enable Your SSL Certificate
If you are renewing a certificate, or if you have more than one certificate in the AD FS Personal Store, you need to tell the AD FS service which certificate to use. If you don’t, AD FS service may pick the wrong or expired certificate.
On your Windows 2012/2012R2 AD FS server, open the AD FS management console as an admin.
From the Windows Start screen, type ad fs management.
Right-click on AD FS Management.
In the menu at the bottom of the screen, click Run as administrator.
In the User Account Control window, click Yes to allow the program to make changes to the computer.
In the AD FS Console window, in the console tree, expand Services, right-click on the Certificates folder, and select Set Service Communications Certificate.

This time in the Windows Security window, select the new SSL Certificate that you just assigned to the AD FS Service in the previous section and then, click Click here to view certificate properties.
In the Certificate window, on the Details tab, in the Show drop-down list, select Properties Only.
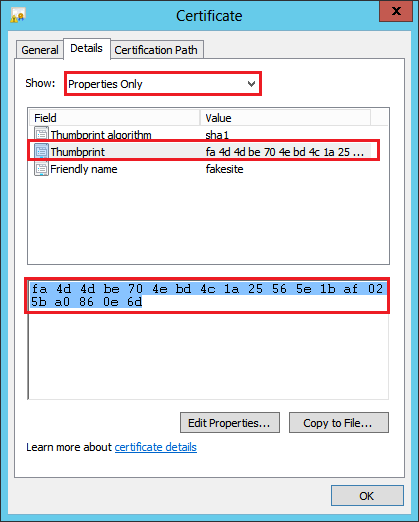
In the list below, select Thumbprint.
In the box below the list, copy the thumbprint.
In a text editor, such as Notepad, paste the thumbprint and then remove all the spaces from the ends or middles of the thumbprint string.

On your AD FS server, open Windows PowerShell as an admin.
From the Windows Start screen, type Windows PowerShell.
Right-click on Windows PowerShell.
In the menu at the bottom of the screen, click Run as administrator.
In the User Account Control window, click Yes to allow the program to make changes to the computer.
In the Administrator: Windows PowerShell window, run the following command:
Set-AdfsSslCertificate –Thumbprint xxxxthumbprintofthenewsslcertxxxxx
Restart the AD FS Service.
To confirm that the certificate is enabled, in PowerShell (run as administrator), run the following command:
Get-AdfsSslCertificate –Thumbprint xxxxthumbprintofthenewsslcertxxxxx
Your SSL Certificate should now be enabled.
Test Your Installation
If your website is publicly accessible, our DigiCert® SSL Installation Diagnostics Tool can help you diagnose common problems.

