How to Build a PKI That Scales: First 3 Considerations [Interview]

In this interview with Darin Andrew, Senior PKI Architect at DigiCert, we pose as the head of engineering at a medium-sized company to ask him how we can build a PKI that’s ready to scale.
Are you confident you have the right technologies in place to meet the security needs of your company over the next 5–10 years? If not, you’re not alone. Only 27 percent of information security decision-makers said they were extremely or very confident when asked this question by IDG Research Group.
Seeing that so many security professionals lack confidence, we sat down with our very own Darin Andrew. Darin talks with customers every day about how they can get their security systems to a point where they’re confident they have not only the right technologies in place, but also the right systems, procedures, and personnel.
For our first interview with Darin, we asked him about the high-level overview of PKI. We asked him about the main ways in which PKI is typically used, and how medium-sized companies can begin to build an enterprise-level PKI. Here’s what he taught us:
Okay, Darin, I was just hired as director of engineering at my company. Management has tasked me with enhancing cybersecurity. Where do I start?
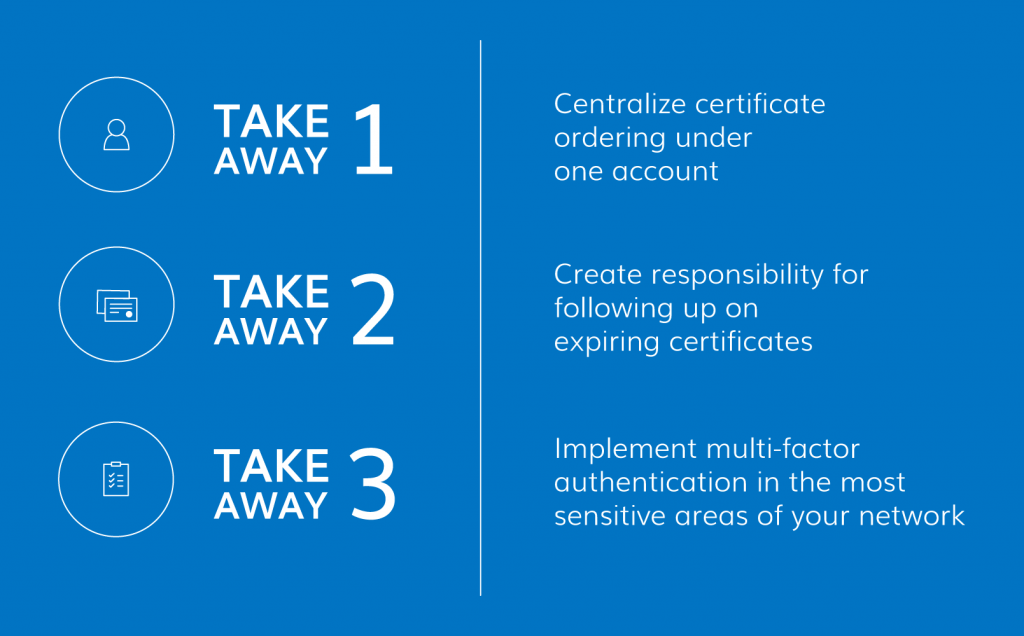
DA: The first thing you want to know is whether all certificates are being ordered from the same account. Imagine the nightmare it creates if certificates aren’t being ordered from the same account. How do you get reliable reporting on expiring certificates and volumes of certificates that are out there? Even just for logistics purposes, do you know whether a certificate should be issued at all? What report can you view that tells you how your domain name is being used on all the certificates out there?
So, first off, get everything under the same account with oversight by someone like a PKI administrator or a team of people who do the PKI administration. But there needs to be a head of that team that has oversight and makes sure you’re following the right practices.
So, now all my certificates are being ordered under the same account. What’s next?
DA: The next thing I would do is make sure there’s responsibility for following up on every expiring cert. So, if you’re consolidating into a single account, and you’re getting reliable reports on certificates that are expiring, you need people following up on certificates that are 30, 60, or 90 days out from expiring. They’ll need to go find out which server that certificate was for and apply a new one if needed. The last thing you want is a certificate expiring and bringing down services, so this is a real issue for companies out there.
All my certificates are being ordered under one account, and I’ve delegated responsibility for following up on expiring certificates. Now what?
DA: Now, I would focus on including multi-factor authentication (MFA) to protect the most sensitive areas of your cybersecurity. A big one for most companies is setting up multi-factor authentication into VPN. This makes it so a hacker would not only have to compromise the user’s password, but also have physical possession of the user’s device. If you take DigiCert as an example, we use a minimum of two-factor authentication for accessing sensitive assets, and, on occasion, even more than that. Every company has key areas of its business that it doesn’t want compromised. Maybe it’s a company wiki; maybe it’s a VPN; the point is that your internal information needs to be protected beyond the standard user name and password.
I’d also set up automation for the enrollment of those certificates, whether you use Microsoft AD Autoenrollment or something like SCEP that handles the renewals as well. This will make it so you don’t have to worry about users’ certificates expiring. Instead, they’ll automatically get new certs for multi-factor authentication before the cert expires.
The number of enterprises using MFA has been skyrocketing as of late, according to InfoSecurity. Although only 66 percent of organizations were using MFA at some level in 2015, that number grew to 93 percent a year later.
The number of enterprises using MFA companywide jumped from 30 percent (2013) to 36 percent (2014) to 51 percent (2016).
So, if these are the main three things a company should be doing using PKI, what would come next?
DA: Well, now that you understand that these three items are critical to PKI (the “what”), you’ll want to consider how to implement each (the “how”).You’ll want to consider how to:
- Automate your SSL processes to eliminate inefficiency
- Decide between a private, public, or hybrid PKI
- Decide between a hosted or on-premise CA
- Use client certificates to secure and encrypt email
- Stay compliant with security standards
I imagine these will be topics we’ll dive more deeply into during future interviews.
Darin’s right—we have already lined up interviews to dig into each one of those topics. But for now, here are your takeaways:
This blog post is part of a series. To learn more, read parts two, three, and four.





