Understanding the New
Code-Signing Certificate Validity Change
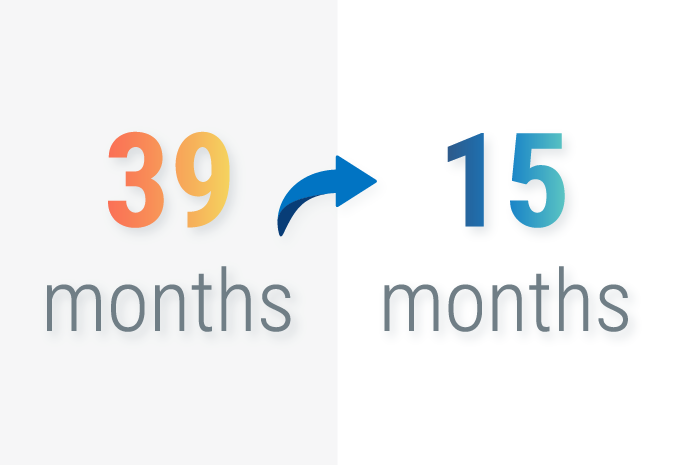
The CA/Browser Forum has approved a new ballot that reduces the maximum validity period for publicly trusted code-signing certificates from 39 months (roughly three years) to 460 days (about 15 months). This change will take effect March 1, 2026, and represents the industry’s continued effort to encourage automation and strengthen software supply chain security (SSC).
For organizations that rely on code signing to prove the authenticity and integrity of their software, this change raises important operational questions: What does it mean for us? Who will this update impact most? And perhaps most importantly, what should we do to prepare?
From TLS to code signing: The shift to shorter validity
The Certificate Authority/Browser Forum (CA/BF)—the body of certificate authorities, browser vendors, and platform providers that define the rules of trusted certificates—regularly reviews standards regarding digital certificates. Shorter validity periods ensure that cryptographic material is rotated more frequently, reducing exposure if a private key is ever compromised.
More frequent renewals also help organizations keep keys current, comply with modern standards, and adopt stronger controls for how and where private keys are stored and used. They provide a natural cadence for assessing cryptographic readiness and planning future transitions to stronger or quantum-safe algorithms.
In recent years, we’ve seen TLS/SSL certificate lifetimes drop down to 398 days. They’ll drop again to 200 days in March 2026 and 100 the following year before plummeting to 47 days in 2029.
Now it’s code signing’s turn. The new 460-day limit aligns code signing with this short-lived certificate model—a model designed to minimize risk through regular key rotation and faster adoption of stronger security practices. The change also reflects the reality that software and signing environments change much faster
than they used to.
Who will be affected?
Every organization that signs code with a publicly trusted certificate will be impacted by the new 460-day limit. The level of disruption depends largely on how you manage your private keys and signing workflows.
Hardware-token users
Organizations that store private keys on the Federal Information Processing Standard (FIPS) or Common Criteria-compliant hardware tokens (e.g., USB tokens) will face the most operational change. Beginning March 1, 2026, certificates will need to be replaced every 15 months. Many teams currently procure multi-year tokens and renew less often; that renewal cycle will now need
to shorten considerably.
Customers using cloud-based signing services
Those who sign code through a managed signing platform like DigiCert® KeyLocker or Software Trust Manager will experience minimal disruption. Because these services already automate certificate renewal and key rotation in secure environments, the shorter lifetime should be nearly
invisible to users.
Developers with legacy build systems
Older CI/CD pipelines that rely on manual processes or static certificates will require updates. These environments can be complex to modernize, but this change creates a clear incentive to automate and integrate with modern signing APIs, reducing future maintenance overhead and risks.
What this means for customers
The most immediate takeaway is that code-signing certificate renewals will happen more often. While this might seem like extra work, it’s ultimately a positive move toward resilience and security.
Customers should expect:
An annual renewal cadence: Build your internal calendar around a 12-month cycle so you can budget and schedule renewals before certificates expire.
More frequent hardware updates: If you use tokens, work with your security team to evaluate whether a cloud-based signing service could simplify management.
An increased focus on automation: Manual certificate management is unsustainable as lifetimes shrink. Automation reduces the risk of outages and enables seamless rotation.
Tighter alignment with SSC best practices: Frequent renewals reinforce controls that protect against malware injection and tampering.
How to prepare for shorter code-signing certificate lifetimes
This change offers an opportunity to modernize your signing infrastructure—not just to stay compliant, but to improve security and efficiency. Here are key actions to take as you prepare for the new 15-month validity period.
- Inventory your current certificates and renewal dates. Know what you have, where it’s used, and when it expires. Visibility is the first step toward avoiding unexpected interruptions.
- Evaluate your key storage method. If you still rely on physical tokens, start exploring cloud-based or managed signing solutions. These services eliminate token logistics and enable automated renewals under the new rules.
- Automate renewal and signing workflows. Integrate certificate issuance and rotation into your build pipelines using the Automated Certificate Management Environment (ACME) protocol or DigiCert APIs. Automation ensures continuity and reduces human error.
- Update documentation and policies. Revise internal security and operations policies to reflect the 15-month maximum validity. Clearly define ownership for certificate renewal, key rotation, and revocation.
- Engage with your CA early. Your certificate authority can help you plan the transition, recommend automation strategies, and ensure your environment meets the new standards well before enforcement begins.
Embracing the next phase of digital trust
The move to 460-day certificates isn’t a disruption—it’s progress. It continues the industry’s ongoing evolution toward shorter lifespans that strengthen security, encourage automation, and reduce risk.
By March 2026, organizations that embrace automated, cloud-based signing services will adapt almost effortlessly, while those relying on manual or legacy processes may struggle with constant renewals and operational friction.
Now’s the time to modernize your approach to code signing—not simply to meet new requirements, but to reinforce the integrity of every release.
Ready to take the next step? Connect with an expert to learn how DigiCert Software Trust Manager can help you simplify renewals, secure keys, and modernize your signing workflows before the 460-day transition takes effect.




