
The fourth quarter has always been a stress test for the internet. As year-end commerce peaks, travel surges, and millions of new devices come online, demand for DNS resolution, bandwidth, and application availability rises sharply. At the same time, security teams often operate with reduced staffing and compressed response windows—conditions that adversaries understand well.
DigiCert’s Q4 2025 RADAR Brief confirms that this seasonal pressure is no longer just about volume. Across DNS, DDoS, and web applications, attackers pushed infrastructure harder, ran campaigns longer, and coordinated activity across layers in ways that challenge traditional definitions of resilience.
The data points to a clear shift: Availability is no longer threatened by short spikes alone, but by sustained, multi-layer pressure designed to test endurance.
Record demand meets rising DNS pressure
DNS traffic climbed steadily throughout Q4, closing December at 4.75 trillion authoritative queries, up roughly 10% from October. On its own, that growth reflects a healthy, active internet driven by global commerce, streaming, and connected devices.
But beneath the surface, the signals were more complex.
Resolution success rates softened slightly as NXDOMAIN responses increased, a pattern often associated with automated querying, speculative lookups, or enumeration behavior. More notably, DDoS attacks targeting DNS surged dramatically in December, jumping from fewer than 20 monthly events earlier in the quarter to 176 attacks.
This combination—rising demand paired with rising abuse—reinforces DNS’s dual role as both a foundational service and an increasingly attractive attack surface. When DNS is pressured, the impact cascades upward, affecting applications, APIs, and end-user experience simultaneously.
The takeaway for defenders is not that DNS failed—it didn’t—but that DNS resilience is now inseparable from overall security posture.
DDoS moves from disruption to endurance testing
If DNS showed mounting strain, DDoS activity in Q4 revealed a decisive escalation in attacker ambition.
After relatively contained activity in October and November, December marked a step-change. Total attacks more than doubled month over month, peaking at 2,200 events, while mega attacks (100+ Gbps) increased sharply. The largest observed attack reached 2.02 Tbps, firmly establishing terabit-scale DDoS as an active, not theoretical, threat.
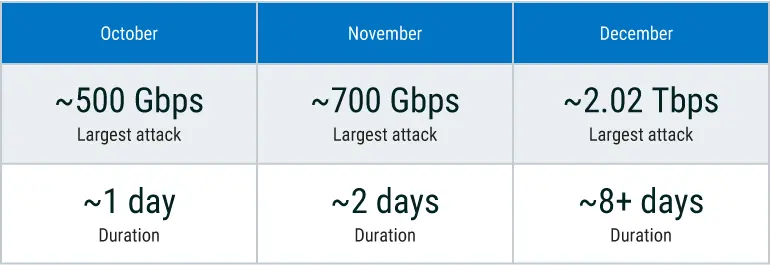
Just as important as scale was persistence. Attack durations stretched from hours into days, with the longest event running more than eight days. These weren't smash-and-grab disruptions; they were sustained campaigns designed to exhaust defenses, teams, and mitigation capacity over time.
Attack patterns shifted as well. Targeted floods dominated, while carpet-bombing attacks declined, signaling a preference for focused pressure on specific services and providers rather than broad subnet saturation.
Taken together, Q4 data shows DDoS evolving from episodic disruption into a test of operational stamina—especially for infrastructure and service providers whose downtime ripples outward.
Application-layer threats narrow but don’t disappear
At the application layer, UltraWAF telemetry told a different but complementary story.
Overall malicious volume declined in December compared to earlier in the quarter, yet automated activity persisted at scale. Bot violations remained steady, and cookie-based manipulation accounted for nearly half of detected threats, underscoring how attackers continue to probe session handling, authentication logic, and application state.
Rather than broad noise, Q4 showed more selective exploitation. Threats concentrated on high-value industries like travel and financial services, where availability and transaction integrity are tightly coupled to revenue and trust.
This narrowing of focus aligns with trends seen at the network layer: Attackers aren't retreating—they’re refining.
What Q4 makes clear about modern attacks
Viewed together, Q4’s DNS, DDoS, and WAF data reveals a consistent pattern: Attackers are no longer treating infrastructure layers in isolation. Campaigns traverse DNS, network, and application surfaces, probing for weak seams and compounding pressure where systems intersect.
Volume still matters—but endurance matters more.
For security leaders, this reframes resilience. It’s no longer defined solely by peak capacity or one-time mitigation success, but by the ability to sustain operations under prolonged, adaptive stress.
Resilience is now the trust metric
The latest RADAR Brief reinforces a shift that’s been building throughout the year: Digital trust is increasingly measured by resilience.
Organizations that weathered Q4 successfully weren’t just those with strong point defenses, but those with integrated visibility, cross-layer coordination, and partners capable of absorbing pressure without degradation over time.
Explore the full RADAR Brief for deeper analysis of the attack patterns, industry targeting, and defensive considerations that shaped the final months of 2025.




