
For decades, public key infrastructure (PKI) was the quiet utility of the internet—essential and reliable, but largely static. You issued a certificate, installed it, and didn’t think about it again for years. Like water or electricity, PKI's value only became noticeable when it didn’t work.
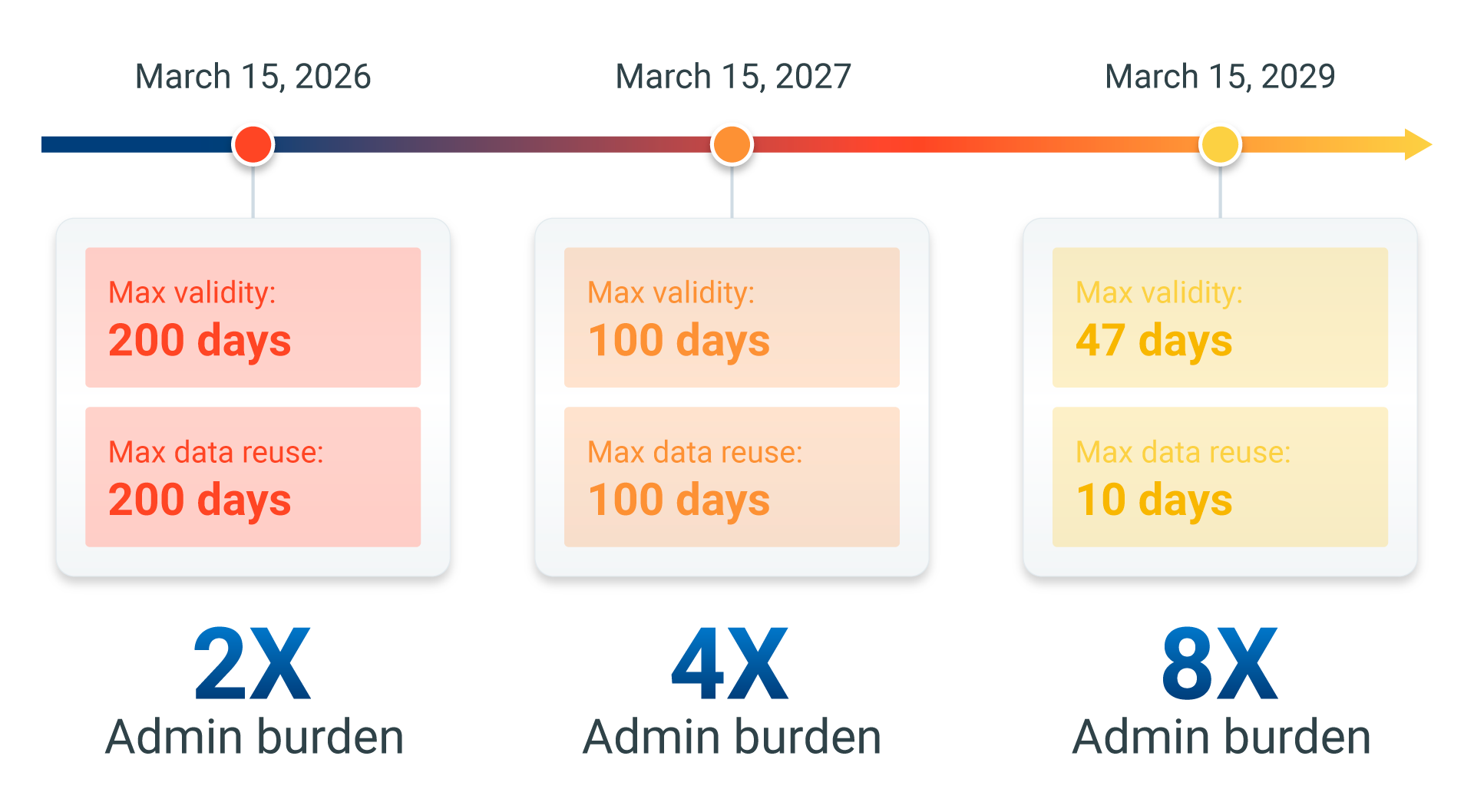
That era is ending. With the CA/Browser Forum and major platform providers like Apple moving toward 47-day public TLS certificate lifecycles by 2029, certificate management is no longer a background task. Shortened lifespans compress operational timelines and expose brittle, manual processes that were never designed for this level of velocity.
In a 47-day world, the question isn’t whether organizations should modernize their approach to PKI—it’s whether they can do so fast enough, and with the right partners in place.
The mathematics of chaos: Why 47 days breaks the old model
To understand why strategic alliances are forming, you have to look at the math:
The old world: A Global 2000 organization with 10,000 certificates valid for 398 days manages roughly 25 renewals per day. With enough planning, that’s manageable.
The new world: That same organization operating on 47-day lifecycles now faces more than 200 renewals per day—an almost eightfold increase in operational volume.
This isn’t an incremental change—it’s a structural one. An eightfold increase in renewal velocity collapses any process that relies on manual touchpoints, maintenance windows, or human coordination.
In a 47-day lifecycle, if a human has to touch a certificate, the system has already failed. At this scale, reliability depends entirely on zero-touch automation across issuance, renewal, installation, and validation. Anything less guarantees outages, security gaps, or both.
But automation alone isn’t the end of the story. Certificate lifecycles span infrastructure platforms, security tools, and operational teams that were never designed to move in lockstep. As velocity increases, those dependencies become impossible to ignore.
The importance of strategic alliances in a 47-day lifecycle
No single vendor can solve the 47-day challenge in isolation. The velocity of certificate operations exceeds what any standalone platform—or internal team—can reliably manage on its own.
This reality has given rise to a new wave of strategic alliances: formal, contracted partnerships across certificate authorities, certificate lifecycle management platforms, cybersecurity technology vendors, and service providers, designed around shared operational outcomes rather than individual tools.
As certificate lifespans shrink, interdependencies across infrastructure, security tooling, and service delivery become unavoidable. Automation only works when those dependencies are addressed collectively.
In a 47-day world, strategic alliances aren’t an optimization—they’re a prerequisite for scale and reliability.
The operating model for a 47-day PKI ecosystem
Strategic alliances are only effective when they operate within a clear model. In practice, a sustainable 47-day PKI ecosystem takes the shape of a three-part operating structure:
- The technology layer (CA + CLM): Provides the cryptographic trust anchor and the automation framework required to issue, renew, and rotate certificates at machine speed. This layer establishes policy enforcement, lifecycle control, and consistency across environments. At DigiCert, this orchestration is delivered through Trust Lifecycle Manager, which connects certificate issuance with automated workflows and partner integrations across the trust ecosystem.
- The operator (MSSP): Owns day-to-day execution. Managed Security Service Providers absorb operational risk by monitoring automation, validating outcomes, and managing exceptions, ensuring renewals complete successfully without constant customer oversight.
The architect (GSI): Designs the enterprise-wide strategy. Global Systems Integrators unify PKI silos across cloud, on-prem, DevOps, IoT, and legacy environments, while defining the governance, ownership, and compliance frameworks that automation depends on.
No single role succeeds independently. The technology enables scale, the operator sustains reliability, and the architect ensures long-term adaptability.
3 ways strategic alliances show up in practice
The following examples illustrate how strategic alliances function in practice, addressing the most common operational bottlenecks created by short-lived certificates. Each represents a critical layer of the ecosystem, working together to sustain reliability at machine speed.
1. The “last mile” alliance: Load balancers and application delivery
In a 47-day world, the most common failure point isn’t certificate issuance—it’s installation. This work typically occurs at the edge, on application delivery controllers (ADCs), load balancers, and firewalls.
Historically, updating certificates in these environments was a manual, high-risk process requiring maintenance windows and careful coordination. Repeating that hundreds of times per day is operationally impossible.
Through strategic alliances, DigiCert has built certified integrations with leading ADC and load balancer platforms. These integrations enable certificates to be renewed, deployed, bound, and validated automatically using native APIs—without human intervention.
The result is a shift from bottlenecks to enforcement points, where certificate rotation happens invisibly to application owners and without disrupting availability.
2. The nervous system: SIEM and observability platforms
As certificate operations accelerate, so does telemetry. Automated renewals generate thousands of events that must be monitored in context.
In a manual world, visibility came from expiration alerts. In an automated world, failures can occur silently unless they surface through existing security operations workflows.
Strategic alliances between certificate lifecycle management platforms and SIEM or observability tools close this gap. Certificate events flow directly into monitoring systems, where they’re correlated with broader security and operational signals.
This enables exception-based response. SOC teams don’t watch certificate dashboards—they’re alerted only when automation fails and intervention is truly required.
The service layer: Operationalizing the ecosystem
While DigiCert provides the core PKI and lifecycle technology, service partners play a critical role in operationalizing it at scale. In a 47-day lifecycle, these partners generally fall into two distinct—but complementary—roles:
Managed Security Service Providers (MSSPs): Operational execution
- Deliver managed certificate lifecycle services as an outcome, not a toolset
- Monitor automation, validate renewals, and manage exceptions
- Absorb day-to-day operational risk so internal teams don’t have to
- Ensure certificates aren't just issued, but correctly installed and activated across environments
Global Systems Integrators (GSIs): Transformation and governance
- Unify fragmented PKI environments across cloud, on-prem, DevOps, IoT, and legacy systems
- Design automation strategies that scale across the enterprise
- Define ownership, policy, and compliance frameworks before automation is deployed
- Prepare organizations for long-term cryptographic change, including post-quantum migration
Together, MSSPs and GSIs ensure that automation delivers reliability today while setting the foundation for future crypto-agility.
PQC: The next forcing function
The move to 47-day certificate lifecycles isn’t just about reducing risk—it’s a rehearsal for post-quantum cryptography (PQC).
NIST has standardized the first quantum-resistant algorithms, but migrating to them will be one of the most complex cryptographic transitions in history. Every system that relies on cryptography must be discovered, assessed, and updated—often using hybrid approaches that combine classical and quantum-safe algorithms.
If an organization can't reliably automate certificate rotation every 47 days, it will struggle to execute a successful PQC migration.
Strategic alliances make this transition possible by providing the agility to evolve cryptographic foundations without breaking applications or operational workflows.
Turning the 47-day sprint into a strategic advantage
The organizations that succeed won’t be those with the largest internal PKI teams. They’ll be the ones that design for velocity—leveraging strategic alliances to reduce operational risk today while building the crypto-agility needed for what comes next.
To understand how this shift applies to your environment, it’s worth examining how certificate lifecycle automation integrates across your existing infrastructure and partner ecosystem. Explore DigiCert’s integrations to learn more, or get in touch to discuss how strategic alliances can support your OpSec and PKI strategy.




