The 3 keys to automated certificate lifecycle management

New technologies and ever-increasing connectivity have made many people’s jobs easier. But for most network administrators, the opposite is true.
Organizations rely on network admins to ensure web servers and load balancers provide both redundancy and high availability while keeping them protected against bad actors. They also have to guarantee the apps and data running on their servers and load balancers remain secure—without taking them offline.
For years, the people shouldering this burden have used a combination of spreadsheets, scripts, and point tools to manage the lifecycles of the TLS certificates that safeguard connections and communications. This type of manual certificate management has always been time-consuming. But it’s becoming increasingly unsustainable.
The solution? A certificate lifecycle platform that automates the management of TLS certificates from procurement to renewal and revocation.
Let’s explore why automated certificate lifecycle management (CLM) is moving from nice-to-have to necessity and which capabilities make it possible for network admins to successfully manage the massive number of certificates they’re responsible for.
Shorter certificate lifespans, longer lists of certificates to manage
The maximum lifespan of public certificates has been dropping for over a decade, from five years in 2012 to 398 days in 2020, with the possibility of decreasing to just 90 days if Google has its way.
Shortened lifespans mean certificates expire much more quickly than they used to. And when they’re managed manually, an expiring certificate is easy to miss, putting the organization at risk of an outage—or worse, a data breach.
Further complicating matters is the move many large organizations have made to migrate from traditional data centers to distributed, complex IT environments, leading to an explosion in the number of TLS certificates enterprises need to manage. The words “digital certificate” are now often used interchangeably with “machine identity” because the definition of “machine” has broadened in today’s hybrid IT world.
A machine can now be anything from a traditional physical server or PC to a mobile or IoT device, website, online app made up of microservices, container, or cloud instance. What each of these machines has in common is the need for a unique machine identity to safely communicate with other machines. And network admins have the increasingly cumbersome task of managing each and every identity.
The 3 capabilities of an effective certificate lifecycle platform
You probably already know that a good CLM solution needs to work across your entire enterprise. But what specific capabilities enable a network admin to manage their complete certificate inventory?
Here are three things to keep in mind.
1. Native integrations with third-party network devices
A typical cluster of web servers or load balancers can host thousands of applications, each of which is made up of hundreds of microservices. Every individual server, app, and microservice requires its own machine identity to properly authenticate with other identities and ensure the network is secure.
To keep track of every machine identity, your organization needs to maintain a complete, up-to-date certificate inventory. But not all CLM solutions provide native integration with network devices, which means you need multiple ways to automate certificate management.
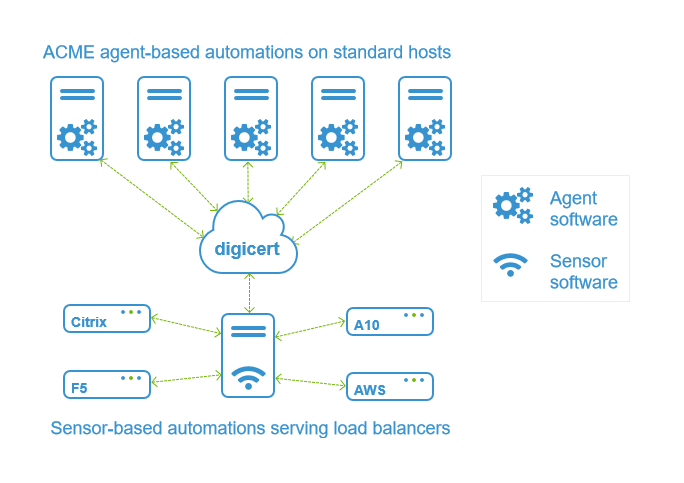
For web servers, load balancers, and other network appliances, you need locally installed agents and API integrations (sensors) that reliably connect every device with the CLM platform. If a solution can’t ensure these integrations work seamlessly, you’ll risk spending more time troubleshooting than you would save with automation.
An effective CLM solution includes native integrations with every device so you can reliably manage all the certificates associated with these architectures, ideally providing its own complete CLM automation architecture that runs seamlessly with web servers and load balancers.
A solution like DigiCert® Trust Lifecycle Manager supports all the diverse workflows and targets that network admins have to contend with, which is especially crucial given the need for network devices to provide continuous availability.
2. Profiles for automating certificate deployment
Flexibility is important when automating certificate lifecycle management. You may want to use different certificate lifespans for internal (private) versus external (public) web servers, for example. But most network admins don’t have the public key infrastructure (PKI) expertise to configure these actions.
That’s where profiles come in. Profiles follow a predefined set of rules to determine how digital certificates are issued, managed, and used. An effective CLM solution provides templates with preset configurations that you can then apply to define certificate properties such as type, validity, and trust hierarchy to enforce different configurations for different use cases. For example, you can create profiles to define separate configurations for public web server certificates, internal device and service authentication, and employee access to apps on corporate Wi-Fi networks.
Automating workflows will also help you identify and remedy security and compliance issues. For example, automation may reveal that a certificate was procured using an unapproved certificate authority (CA) like Let’s Encrypt, allowing you to replace it with a DigiCert certificate before a problem arises. You can also time certificates to renew only when traffic is low, ensuring a renewal doesn’t inadvertently bring down your app during a peak season like Black Friday.
3. Continuous availability
Network admins know security is the foundation for maintaining business continuity. But without a CLM platform that automates certificate management, achieving 100% availability will remain an impossible goal—there are simply too many digital certificates to manage manually, leaving endless opportunities for human error.
A good CLM platform provides full-stack automation from the discovery phase through to the management of TLS certificate lifecycles. By streamlining these myriad processes and reducing the possibility of misconfigurations, network admins will eliminate the risk of downtime because of an errant certificate. The ability to reduce overhead while simultaneously hardening security will allow them to concentrate on the job they were hired to do.
The latest developments in digital trust
Want to learn more about topics like certificate management, enterprise security, and PKI? Subscribe to the DigiCert blog to ensure you never miss a story.




