Java Heightens the Security Requirements for all Rich Internet Applications (RIAs)

Java 7 Update 51 (7u51)
On January 14, 2014, Java released the Java 7 update 51 (7u51), which heightened the authentication and authorization security requirements for all Rich Internet Applications (RIAs). You are now required to sign all code for Applets and Web Start applications with a code signature from a trusted Certificate Authority (CA). Code signatures allow end-users to identify the publisher, to check the date that the code was signed, and to verify that the original code has not been changed since it was signed.
To enforce code signatures on all Applets and Web Start applications, Java updated the default security slider to block Rich Internet Applications (RIAs) that do not conform to the new security requirements. If Applets and Web Start applications do not have a code signature, they will not run. These changes affect Java applications that start through a Web browser, not standalone Java applications that run outside a Web browser. Note that all existing RIAs must also be updated to meet these new requirements, or they will not run; the required updates should only affect packaging and distribution, not API code.
For additional information about Java’s new security requirements, see New security requirements for RIAs in 7u51 (January 2014).
Code Signing Process (Java .jar Files)
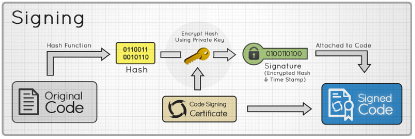
Code signing is the process of creating a bundle that can be used by the Web browser to confirm the author of the code and to ratify that the original code has not been altered or corrupted.
The Java .jar file code signing process consists of the following steps:
-
Download and install the Java Development Kit (JDK).
For more information, visit Oracle Technology Network at http://www.oracle.com/technetwork/java/index.html.
-
Acquire a Code Signing Certificate from a trusted Certificate Authority (CA), such as DigiCert.
To acquire a Code Signing Certificate, do the following:
-
Obtain a Code Signing Certificate from DigiCert.
See the Java Code Signing Certificate Guide (Digitally Sign Code for Java Applets with Integrated Identity Assurance) and Code Signing Certificates pages.
-
Create a Java keystore and CSR (Certificate Signing Request).
See the Code Signing Java CSR Creation and Installation section of the Java Code Signing Certificate Guide page and the Java Keytool CSR Creation page.
-
Install the Code Signing Certificate in the keystore.
See the Code Signing Java CSR Creation and Installation section of the Java Code Signing Certificate Guide page.
-
-
Use Jarsigner to sign your Java .jar files.
See the Signing a Java .jar Files with Jarsigner section of the Java Code Signing Certificate Guide page.
Code Signature Verification Process
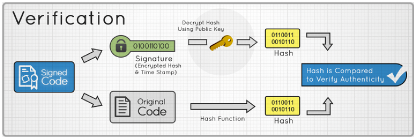
After the Web browser downloads the Applet or Web Start application, it checks for a timestamp, authenticates the publisher and Certificate Authority (CA), and checks to see if the code has been altered/corrupted.
The timestamp is used to identify the validation period for the code signature. If a timestamp is discovered, then the code signature is valid until the end of time, as long as the code remains unchanged. If a timestamp is not discovered, then the code signature is valid as long as the code remains unchanged but only until the Code Signing Certificate expires. The signature is used to authenticate the publisher and the CA, and as long as the publisher (author or developer) has not been blacklisted, the code signature is valid. Finally, the code is checked to make sure that it has not been changed or corrupted.
If the timestamp (or Code Signature Certificate expiration date) is verified, the signature is validated, and the code is unchanged, then the Web browser admits the Applet or Web Start application. If any of these items do not check out, then the Web browser acts accordingly, with actions dependent on its level of security.
Code Signing Support
- SSL Plus
- SSL Certificates
- Wildcard SSL
- Multi-Domain
- Extended Validation SSL