The Security Benefits of Audit Logging

As an IT administrator, knowing the precise sequence of activities that affect a specific operation, procedure, or event within a company is very valuable. This is where audit logging (sometimes called event logging or system logging) comes in. Logging creates an “audit trail”—a security-relevant chronological record, or set of records, that documents an organization’s digital footsteps day to day. Keeping detailed records of daily activities allows further visibility into employees' actions and helps to keep that company more secure. For example, audit logs act as a detective control because their trails provide evidence if a hacker or user engages in unauthorized activity.
Audit logging is also helpful when it comes to SSL Certificate management. If a certificate is misissued, lost, or needs to be renewed, audit logging gives administrators and other users the ability to retrace their steps. Having a log of user activities helps companies remain organized and also helps when dealing with unforeseen circumstances, including security violations, performance problems, and system flaws.
Audit Logging Reinforces Enterprise Security
This article from WeLiveSecurity states “logging user actions can help [companies] improve security in a variety of ways” because it provides a way for administrators to “reconstruct events, detect intrusions, and analyze problems such as poor performance or unexpected system behavior.” The following includes other ways audit logging can reinforce an enterprise’s security.
Detect Security Breaches
Having detailed audit logs helps companies monitor data and keep track of potential security breaches or internal misuses of information. They help to ensure users follow all documented protocols and also assist in preventing and tracking down fraud. Any sort of intrusion can be detected in real-time by examining audit records as they are created. Importantly, to maximize the security benefits of audit logging, the logs should be reviewed often enough to detect security incidents as early as possible.
Assess System Damages
Audit trails can be used to reconstruct events after a problem has occurred. “Damage can be more easily assessed by reviewing audit trails of system activity to pinpoint how, when, and why normal operations ceased,” according to The National Institute of Standards and Technology in outlining how and why organizations should use audit logging.
Aid in Recovery Processes
Understanding how and why a system crash or an intrusion occurred is pertinent to avoiding similar outcomes in the future. Audit logs can help in situations regarding data loss or corruption by allowing administrators to reconstruct data files through the changes recorded in the logs.
Audit Logging with CertCentral®
DigiCert CertCentral® is a platform created to consolidate certificate monitoring, SSL deployment, certificate inspection, and PKI management. With CertCentral®, administrators can also access audit logs within the account. These logs capture important details such as when a certificate is requested, if a certificate is mis-issued, when a certificate is approved, and other actions. 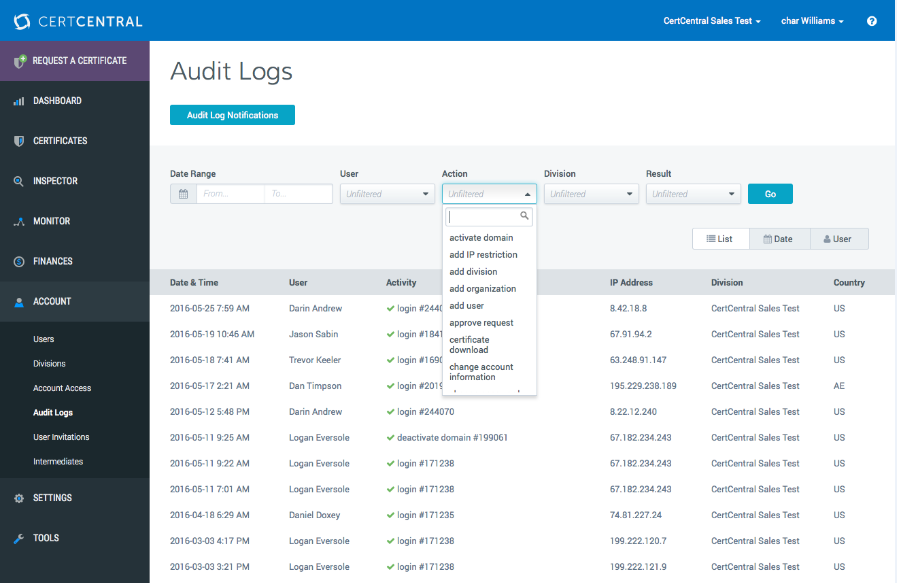
By using the “action” bar, a user can look up recorded logs of their choosing, and all records show the date and time an action was performed, the user that performed the action, the user’s division, and more, with all information organized conveniently on the intuitive dashboard.
Keeping detailed audit logs provides a company many different benefits. If an enterprise makes sure to track and review the logs regularly rather than allowing them to pile up, audit logs can be utilized to reconstruct events, detect intrusions, and analyze problems such as poor performance or unexpected system behavior. Audit logging is an efficient way to help enterprises observe their environment more effectively and to keep their data secure.





