
Quantum computing has amazing promise for the planet—and the power to obliterate the foundational security of the internet.
If you’ve been keeping up with the conversations about quantum, you’ve probably heard about Q-Day—the unspecified-but-inevitable day when quantum computers will be capable of breaking the encryption algorithms we currently rely on to secure the internet and a host of digital processes.
I propose redefining the term to mean the moment you need to be very concerned about the crypto-agility required to prepare your organization for the risks of quantum computing.
That moment is now.
The algorithm quantum is on track to break
The “S” in HTTPS (aka the padlock in your browser) is provided by an encryption protocol called Transport Layer Security (TLS). TLS uses an encryption scheme called asymmetric cryptography that relies on a pair of keys: a public key that encrypts data and verifies digital signatures and a private key that decrypts data and generates digital signatures. The most common asymmetric algorithms today are RSA and ECC.
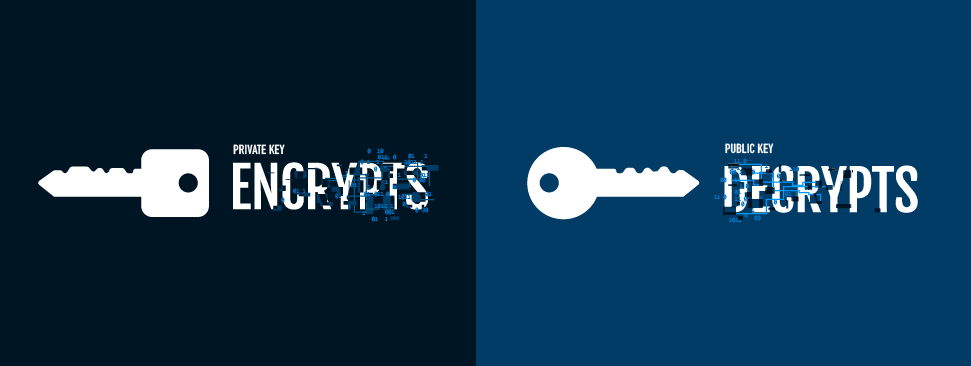
We use asymmetric cryptography to secure network communications, like when you enter your credit card information or taxpayer ID on a website. We also use asymmetric cryptography to protect other encryption keys (key encapsulation) like those used to secure massive databases in clouds and data centers around the world. Put simply, asymmetric cryptography currently secures pretty much everything.
Asymmetric cryptography uses complex math (large prime numbers) that’s very difficult for today’s supercomputers to solve. But quantum computing is exceptional at solving complex math problems. And at some point, quantum computers will have enough power to quickly break the complex math problem that is asymmetric cryptography.
(For more information about asymmetric cryptography, search the internet for “Bob and Alice.” Seriously.)
The question isn’t when—it’s how
No one knows exactly when this will happen, but the “when” isn’t the point. What we should be concerned about—very concerned—is how long it will take to update all our systems to be quantum safe.
And I mean All. Our. Systems.
Medical records. Gas pumps. ATMs. Utilities. Military communications.
This doesn’t mean that everything that’s been secured using RSA encryption will be immediately or simultaneously exposed. Instead, it means that any private key can be derived quickly (think hours, not days), making it easy for attackers to forge or exploit the things it’s securing whenever they want.
How the new PQC algorithms make us quantum safe
RSA and ECC are very general purpose. We use them to encrypt and decrypt information and generate digital signatures to verify the authenticity of messages. That's not the case for the current post-quantum cryptography (PQC) algorithms. Which means specific use cases will require different algorithms.
Twenty-eight PQC algorithms are currently in development, four of which NIST has proposed as standards:
- Crystals-Kyber for encryption key encapsulation
- Crystals-Dilithium for digital signatures
- SPHINCS+ for digital signatures
- FALCON for digital signatures
Regarding computing resources, for example, digital signatures created using RSA 2028 are 256 bits long, while digital signatures created using SPHINCS+ are 17 kilobytes (66 times larger).
You may have noticed NIST is considering three digital signature algorithms for standards. Each has distinct advantages that are useful for different use cases. Dilithium is preferrable for resource-constrained environments like IoT devices. SPHINCS+ uses small keys where storage is limited, but as we showed above it, it generates large signature sizes. FALCON offers fast signature verification, making it ideal for high-performance transaction processing.
The steps your organization can take today
Quantum readiness isn’t something your company can achieve in a day, and there's no one-and-done solution. The best-protected organizations will be crypto-agile, allowing them to replace outdated cryptographic assets without disrupting their system’s infrastructure.
Achieving crypto-agility starts with:
- Creating an inventory of your certificates, algorithms, and other cryptographic assets
- Swapping out encryption algorithms for roots of trust, (e.g., your organization’s private certificate authorities), firmware for long-lived devices, and any other assets that produce signatures that need to be trusted for a long time; and
- Exploring ways to incorporate quantum-safe algorithms into your products.
Putting the “agility” in crypto-agility
Retrofitting the world’s cybersecurity infrastructure to be quantum safe won't be quick—and it will probably take multiple tries. PQC has been in development for many years, but it stands to reason that the first versions approved for use may not stand the test of time.
What’s more, the PQC algorithms aren’t a like-for-like replacement for the algorithms in use today. We’ll have to support more algorithms, and the key sizes and resulting ciphertext (encrypted data) will require more computing resources than the current algorithms.
Q-Day isn’t just today; it’s every day from here on out. That’s why the real endgame is cryptographic agility, with an emphasis on “agility.” True quantum readiness means being prepared to quickly adapt to change—and having security solutions in place that allow you to adapt without causing major disruptions to your business.
The latest developments in digital trust
Want to learn more about topics like crypto-agility, enterprise security, and PQC? Subscribe to the DigiCert blog to ensure you never miss a story.




