.jpg)
Lurking threats in new software
According to Cybersecurity Drive, a study by Gartner found that new software contains 40% to 80% of code from third parties. These include runtime, libraries, components and software development kits (SDKs). This means that you now not only have to worry about the trustworthiness of your own software, but also the unknown threats associated with third-party code. Furthermore, the pressure on companies to release software faster leads you to wonder, where is the time?
Signing your software with a code signing certificate assures your end user that your product has not been tampered with and that it has been signed by a legitimate person or company. What code signing certificates do not confirm is whether your software is secure. When you sign your software, end users are choosing to trust your product based solely on their trust in you as the publisher. So how can you maintain their trust?
Secure software today, vulnerable software tomorrow
In Q2 2023 alone, 7,153 new Common Threats and Vulnerabilities (CVE) were published in the National Vulnerability Database (NVD). In addition, threat actors persistently exploit older vulnerabilities in systems that have not been patched. With this rapid growth rate in vulnerabilities, the challenge lies in staying up to date with known vulnerabilities, understanding the associated risks for each vulnerability, and making informed decisions about whether to resolve them or accept the potential risks associated with the successful exploit of your vulnerability.
A threat management solution
DigiCert has a solution to all these challenges: DigiCert® Software Trust Manager. DigiCert has teamed up with ReversingLabs, a leading software supply chain security company, to introduce a powerful new feature in DigiCert Software Trust Manager called Threat Detection.
Threat Detection allows you to scan all components found in your software prior to release. This enables you to identify vulnerabilities within both your developers' code and any third-party components integrated into your software.
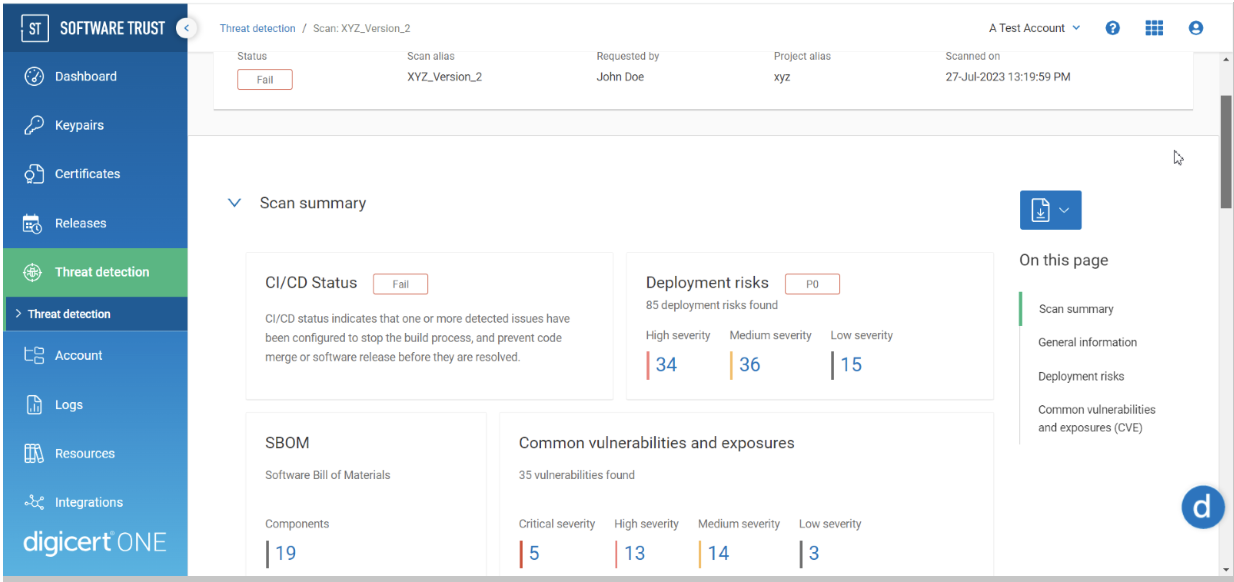
After completing the software scan, an automated tool generates SBOM and SARIF reports by deconstructing the binary to identify third-party, open-source and internally developed dependencies. On May 12, 2021, the U.S. Executive Order 14028 on Improving the Nation's Cybersecurity was published, which mandates that all software used in federal systems must be accompanied by an SBOM. While this may not apply to you, deploying an SBOM along with your software is considered a best practice for building trust through transparency.
Unravel the mysteries of CVEs
The NVD is incredibly useful to identify publicly disclosed CVEs. Relying solely on CVEs for comprehensive vulnerability management, however, has its limitations. CVEs require someone to report a vulnerability. Once reported the CVE assignment team and CVE Numbering Authorities (CNA) vet the vulnerability and assign a CVE ID. This entire process results in delays in publishing "known" vulnerabilities in the NVD for you to find. NVD analysts only begin examining the vulnerability after it is published in NVD; this results in some CVEs being listed without solutions or awaiting vendor patches. These further delays provide attackers with opportunities to exploit vulnerabilities before you have a clear understanding or solution to the issue.
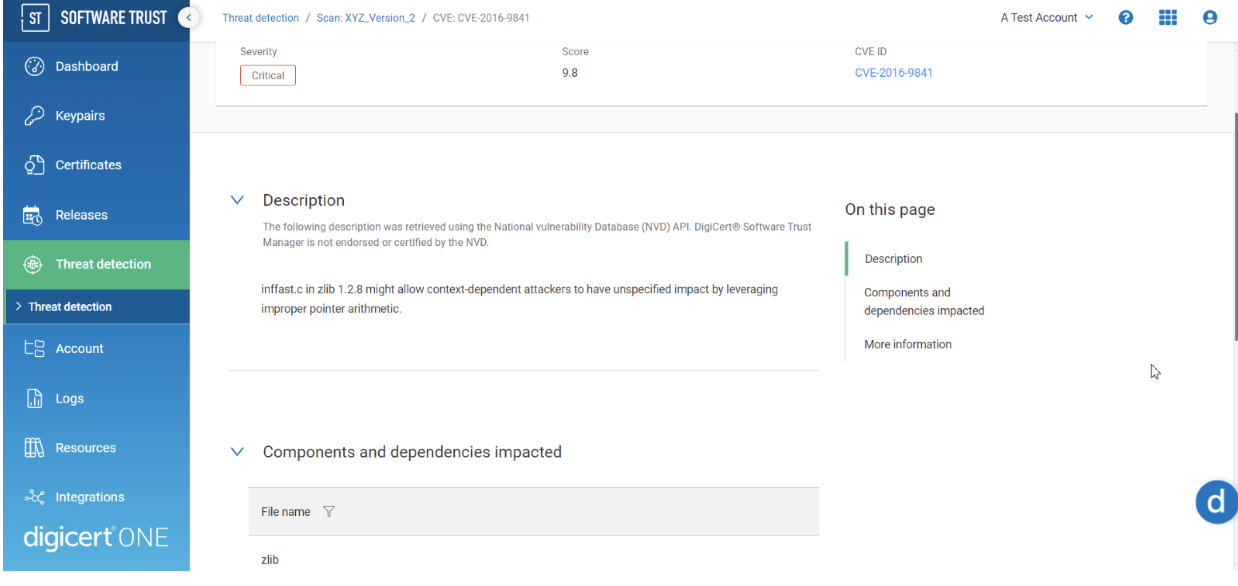
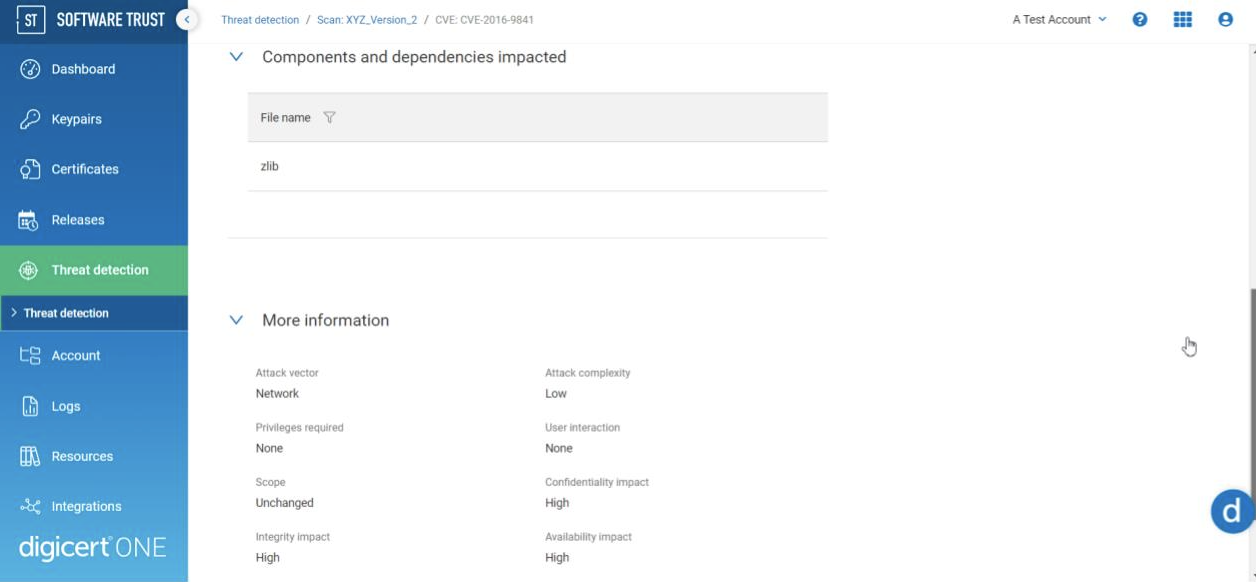
The severity of a CVE is calculated using the Common Vulnerability Scoring System (CVSS), and while this score is often useful, it may not fully represent the potential impact that a successful exploit would have on your organization. Heartbleed is one of the most well-known vulnerabilities in the last decade. The successful exploitation of this vulnerability allowed for theft of the servers' private keys, and yet it was initially assigned a CVSS score of 5 out of 10. To address these issues, DigiCert Software Trust Manager provides a breakdown of the factors contributing to the CVE score as well as supporting documentation on how you can assess these CVE risk factors.
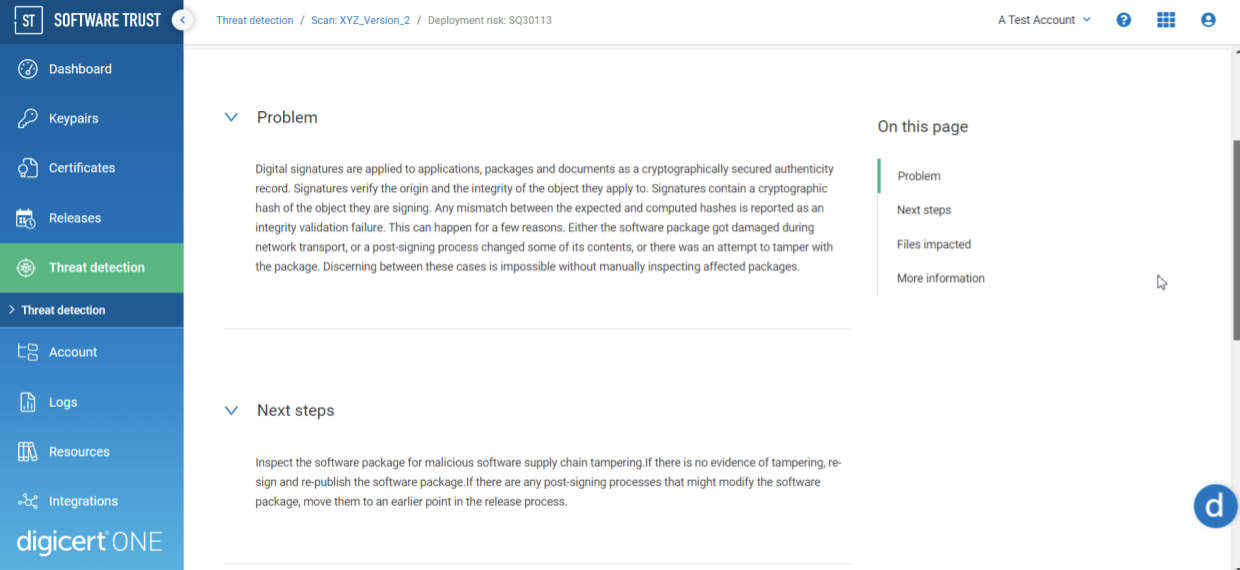
Additionally, DigiCert Software Trust Manager cross-checks your software against CVEs as well as a list of deployment risks compiled and managed by ReversingLabs. This extended analysis by ReversingLabs includes the identification of malware, unencrypted secrets and identifiable information like IP addresses present in your source code.
Identify your most important assets
Assess your organization’s goals, priorities and operational nature to determine which software components are most critical to your organization’s reputation. For example, if your organization adheres to privacy regulations like GDPR, CCPA or HIPAA, ensuring data confidentiality, integrity and availability may be a top priority.
Prioritize your vulnerabilities
DigiCert Software Trust Manager provides a user-friendly graphical user interface (GUI) to display threat detection reports. The report identifies the components within your software that contain specific deployment risks or vulnerabilities. Deployment risks provide a description and solution from ReversingLabs. CVEs provide a description and a link to possible solutions and patches provided in the NVD. The report categorizes vulnerabilities and deployment risks based on their severity and potential impact when exploited.
The severity score associated with CVEs and the priority level associated with ReversingLabs’ deployment risks allows you to make informed decisions, either accepting the risk and proceeding with the software release or using the report to prioritize vulnerability resolution. By assessing the vulnerabilities and deployment risks with the greatest potential impact to your critical assets, you can identify and address the most threatening issues first.
While resolving critical vulnerabilities and deployment risks protects you and your end users from being exploited, resolving non-critical flaws improves the stability of your product and improves user experience. DigiCert Software Trust Manager works to protect your reputation, improve your software’s quality, and protect you and your customers from the repercussions of vulnerabilities being exploited.
Maintaining your customer’s trust
Before releasing your software for consumption, scan your software for vulnerabilities and deployment risks. Prioritize resolving vulnerabilities and deployment risks that would have the most significant impact on your business-critical assets before releasing your software. Boost transparency by shipping the SBOM or SARIF report along with your software to demonstrate the absence of critical vulnerabilities. Lastly, sign and timestamp your software to reinforce trust. This allows your end users to verify whether your software has been compromised after it was signed.
Let DigiCert protect you. Contact DigiCert support to request a demo or refer to our documentation to learn more about Threat Detection.





