U.S. Efforts Underway for IoT Security Labels by Spring 2023
Why IoT Security Labels Could Improve Device Security & Manufacturers Should Prepare Now
As digital transformation has accelerated in recent years, so has our adoption of the Internet of Things (IoT). Experts estimate that there will be about 30 billion IoT devices by 2030. As we are putting more and more of our lives and our trust in the digital, there’s also more need for confidence indicators to provide assurance that our digital interactions are secure.
Currently, consumers are generally unaware of the security of their devices, and manufacturers don’t always make it easy to find information on their device security. But studies show that consumers are willing to pay extra for assurance of device security, and 84% would consider switching vendors if they lose trust in a company’s digital security. That’s why IoT security labels could revolutionize the industry.
What is IoT security labeling?
To provide consumers that information, efforts are underway in the United States to enforce IoT security labeling in devices by Spring 2023. The push comes after the 2021 Executive Order on Improving the Nation's Cybersecurity. Numerous private and public organizations, including big brands like Amazon, Comcast, Google, Intel, LG, Samsung and Sony, met in October to work on an IoT labeling scheme. The White House calls these “easily recognized labels to help consumers make more informed cybersecurity choices” and compares them to EnergyStar but for cyber. The plan is to launch these labels as soon as Spring 2023 for voluntary labeling, but eventually we anticipate that these labels will become mandatory.
A spokesperson for the White House explained, “A labeling program to secure such devices would provide American consumers with the peace of mind that the technology being brought into their homes is safe and incentivize manufacturers to meet higher cybersecurity standards and retailers to market secure devices.”
The U.S. isn’t the first — and won’t be the last — to implement IoT security labeling
Singapore, Germany and Finland already have similar labeling programs in place. Additionally, the EU has recently moved to legislate for IoT as well. In the future, we could potentially see a global standard to prevent fragmentation, or at least minimum requirements in common across various countries as many manufacturers sell devices in various countries across the world, so international collaboration will be necessary.
What will IoT security labels look like?
We don’t know yet exactly what the program will look like, but we have hints from what other countries have done and recommendations from NIST, Google and other researchers. Whatever the label is, it will need to be adaptive, as digital products can be compromised with short notice. Thus, a static label is likely not the best long-term solution.
Singapore approached their labeling with a stars approach, assigning four levels to the increasing implementation of various security best practices (shown below). Germany signed a mutual recognition agreement with Singapore, adopting the same labels. Additionally, Finland has already adopted some aspects of Singapore’s system.
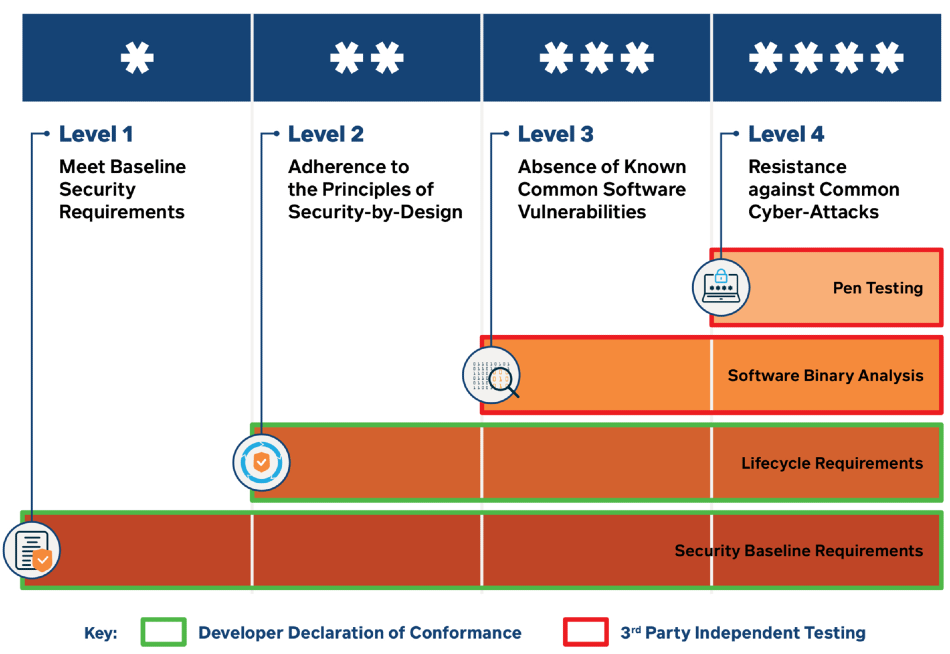
Singapore’s IoT security labeling scheme
However, given the need for real-time updates, most likely the label will contain a QR code where consumers can go for more information. Additionally, it will likely avoid any technical jargon that could confuse consumers. Whatever it is will be more effective than consumers being unaware or individually searching for the name of the product and any vulnerabilities.
NIST has provided IoT security guidelines and recommendations that will inform the labeling program. NIST recommends that the labels show not only information on the device but also the supporting software, which could include apps on phones or controller devices. Additionally, NIST recommends that the labeling have a binary method, meaning that devices either met the requirements or they don’t. Finally, for the software side of things, NIST provides the NIST Secure Software Development Framework for industry baseline security criteria.
Additionally, when considering what the requirements for IoT security labeling will be, we can look to existing IoT industry best practices and standards like Matter. Matter is a new IoT interoperability protocol designed for the smart home that requires AES encryption for communicating across networks, code signing and secure updates. It’s likely that we will see similar best practices applied to the IoT security labeling requirements, especially given that the CSA was involved at the White House Summit on IoT security labels.
IoT security labeling is a major step forward in the industry to giving consumers more knowledge upfront. Just like a nutrition label provides consumers with the health information of food items, an IoT label will show the health of a device’s security so that consumers can make more informed purchase decisions. Ultimately, at DigiCert we think IoT security labeling done the right way is a positive move, as it’s a step towards providing more digital trust, and thus a step towards creating more confidence in our interactions in a connected world.
IoT device manufactures should prepare now for IoT security labeling requirements
For now, manufacturers should seek to comply with the NIST Secure Software Development Framework. Manufacturers can also adopt Matter now, which will help increase their device interoperability and security, and likely prepare them for similar best practices required by the IoT security labeling scheme.
Additionally, companies looking to manage IoT devices at scale should consider DigiCert IoT Trust Manager, which provides a comprehensive, automated workflow for companies to manage their IoT devices with certificate-based security, during manufacturing and at the edge.
DigiCert IoT Trust Manager offers the scalability, flexibility, control and efficiency required for a network of connected devices. Administrators can monitor the entire certificate lifecycle, facilitate secure updates, customize metadata about the device within certificates and remain compliant. Rather than building and maintaining a self-managed PKI, DigiCert IoT Trust Manager automates PKI deployment, making it easy to manage a large network of devices. Admins can customize permissions and access control to segment administration for different user groups. Because DigiCert IoT Trust Manager is part of DigiCert ONE™, it has the flexibility to be deployed on-premises, in-country or in the cloud to meet stringent requirements, custom integrations and airgap needs. Learn more at https://www.digicert.com/iot-trust-manager.





