
Vulnerability & PCI scanning service
Detect Vulnerabilities and Ensure PCI Compliance
Identify potential problems before they become actual
problems. That’s digital trust for the real world.
Website Security is a Relentless Challenge
What you aren’t prepared for could harm your organization
Websites can be exploited by cyberattacks in a variety of ways: from SQL injections to cross-site scripting, malware and certificate misconfigurations. If you’re not proactively safeguarding your digital trust and preventing these security risks, you’re leaving your website open for attacks.

Sites That Aren’t PCI Compliant Are Putting Customer Data at Risk
Some website vendors are simply unaware of the Payment Card Industry (PCI) standard and what is required. But if you’re not protecting your customers’ payment card information under PCI rules then you’re violating your customers’ digital trust and could face costly fines in a data breach.

Most Data Breaches Could Be Prevented With Regular Vulnerability Scanning
Scan for 99.99% of detectable vulnerabilities
Identify misconfigured certificates, servers without dated software or weak certificate keys that may provide an easy entry point for a cybercriminal. Vulnerability assessment provides actionable data and information to fix potential issues before they become a problem. It’s also low maintenance, flexible and 99.99% effective at detecting the latest vulnerabilities.
Enable Your Vulnerability & PCI Scan in Certcentral
Protect your customers personal information and remain PCI compliant so your website is insured against costly attacks. Get weekly or monthly scans, with results sent right to your inbox, so you can remediate issues and keep your website secure.
- Go to your CertCentral account
- Click on Certificates > Order Details > Vulnerability & PCI Scan
- Schedule how often you want the scans to occur
- Get reports emailed directly to your inbox
- Continue to monitor your results
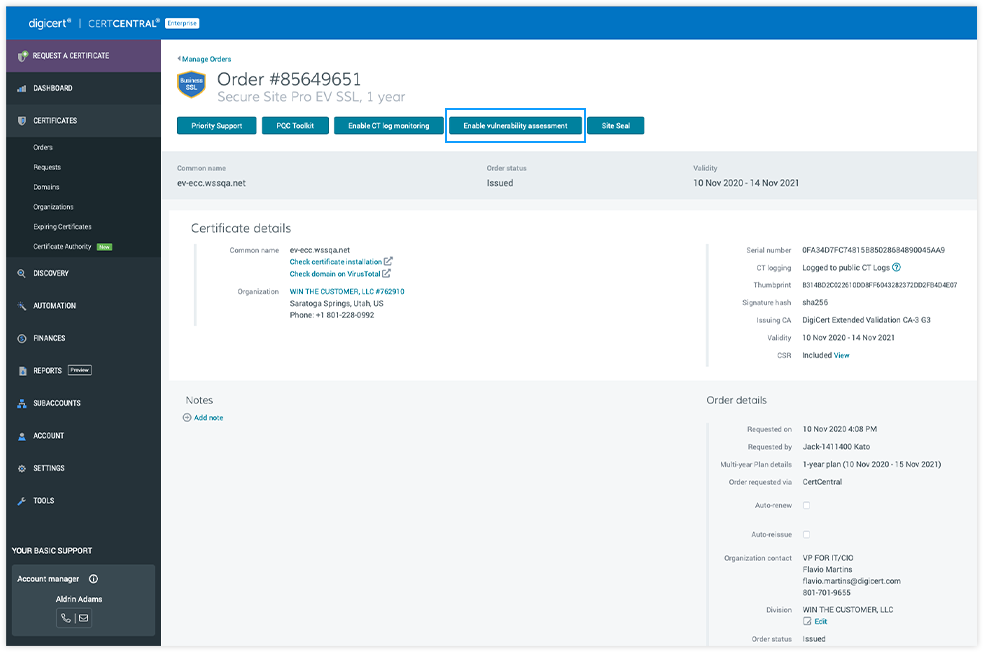
What Your Results Will Look Like
The vulnerability and PCI scan report will be sent to your inbox weekly or monthly, depending on the cadence you selected. Click on “View assessments” in your email to download the report. Get insights and information about:
- Potential vulnerabilities by category and risk level
- Repairs needed to remediate vulnerabilities
- CVSS scores to determine PCI compliance (A score above 4.0 indicates non-compliance)
DigiCert Secure Site Pro TLS Certificates for All-in-one Website Protection
DigiCert Secure Site Pro TLS certificates come with more than just encryption and identity protection. They include all the features to help you ensure your website and servers aren’t vulnerable to malware, outside attacks or fraud. Upgrade your certificate to DigiCert Secure Site Pro and get malware scanning and blocklist checking, in addition to:
Related Resources
INFOGRAPHIC
Smart Seal Infographic: All Pros. No Cons.

WEBPAGE
DigiCert Smart Seal
BLOG
4 Tips for Avoiding Malware

