Attackers have come a long way since using floppy disks to distribute the first known ransomware in 1989. And while the threat had started to feel a lot more real by 2015, many still saw it as a contained risk. Painful, but manageable.
That’s no longer the case. Today, ransomware is something far more dangerous: a coordinated, industrialized threat to business continuity itself. Attackers don’t just lock files anymore—they steal data, stall operations, harass executives, and apply pressure from all angles. One breach can cost millions and cripple supply chains. And in sectors like healthcare, a breach can interrupt critical services that communities rely on.
Let’s look at how we got here—and what you can do to keep your organization safe.
Then vs. now: How ransomware evolved
In the mid-2010s, most ransomware attacks followed a familiar pattern. A user clicked on a phishing email. Files were encrypted, a ransom appeared, and IT teams scrambled to contain the damage. Attacks were disruptive but largely indiscriminate. Many organizations recovered without paying, and most ransoms were in the low five figures.
That era is over.
Today's threat actors behave more like intelligence teams than petty criminals. Rather than immediately encrypting systems, many establish persistence, escalate privileges, and map internal dependencies before taking visible action.
In many cases, encryption is no longer the opening move—it’s the final one. Sensitive data may be exfiltrated quietly for weeks. Identity systems may be probed and monitored. Attackers study business cycles, regulatory pressures, and operational choke points to determine when disruption will create the greatest leverage.
The modern threat landscape
When these intelligence-driven campaigns succeed, the consequences extend far beyond a single compromised system.
In early 2024, UnitedHealth Group’s Change Healthcare subsidiary was hit by ALPHV/BlackCat in one of the most devastating healthcare cyberattacks to date. Attackers gained access through compromised Citrix credentials—without multi-factor authentication (MFA)—and remained inside the environment before launching encryption. The resulting disruption to claims processing reverberated across the U.S. healthcare system, forcing manual workarounds and delaying care for millions. All told, the breach cost UnitedHealth Group more than $3 billion.
Healthcare is particularly vulnerable because of its interconnected infrastructure and operational urgency. Billing platforms, pharmacy systems, identity verification systems, and third-party integrations are tightly coupled. When one node is compromised, the effects cascade across the healthcare supply chain.
This is the defining characteristic of today’s threat landscape: operational dependence. Organizations are no longer isolated targets. They are ecosystems of cloud environments, legacy systems, identity platforms, and software providers. When attackers gain leverage inside that ecosystem, disruption spreads like the plague.
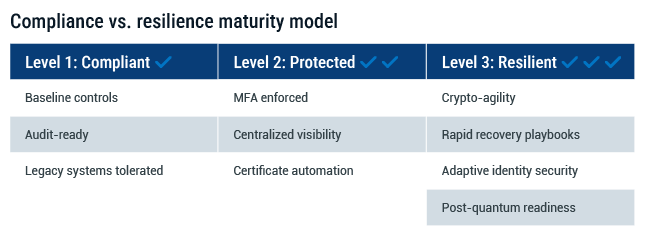
Why compliance is no longer enough
It’s a paradox that keeps playing out: The most heavily regulated industries—healthcare, finance, critical infrastructure—suffer some of the most damaging ransomware attacks. These sectors invest heavily in security, maintain extensive audit trails, and enforce strict compliance requirements. So why do they remain so vulnerable?
Because compliance isn’t the same as security. And it’s definitely not the same as resilience.
Regulations tend to drive uniformity. That’s useful for oversight, but dangerous when attackers are looking for scalable, repeatable vulnerabilities. Compliance frameworks create common baselines, which in turn create predictable environments. For ransomware operators, that predictability is gold, allowing them to design turnkey attack paths that work across entire industries.
Compliance often drives organizations to focus on audit readiness rather than operational security. Legacy systems stay online because they still “meet requirements.” Controls are implemented narrowly to satisfy specific standards, not necessarily to withstand real-world attacks. Investments are prioritized to close findings, not reduce the most urgent risks.
The Change Healthcare attack is a clear example. Despite operating under strict HIPAA mandates, attackers exploited an MFA gap and went undetected for days. The organization was compliant. But it wasn’t protected.
This isn’t a case against regulation—far from it. What it is is a case for recognizing that real security—especially in the age of ransomware—requires going well beyond what’s required on paper. Because sometimes, checking a box just isn’t enough.
How AI and quantum are changing the game
Ransomware is no longer just evolving in volume—it’s evolving in intelligence. As attackers adopt emerging technologies, the risks are becoming harder to predict and more difficult to contain.
Smarter, stealthier attacks with AI
Ransomware groups are shifting tactics. Rather than relying solely on loud, immediate disruption, many now prioritize stealth, persistence, and long-term access inside compromised environments.
Malicious actors continuously adjust their tactics, techniques, and procedures (TTPs) to evade detection and remain under the radar. Defense evasion and persistence techniques allow them to maintain silent residency in a network, exfiltrating sensitive data over time before launching encryption—or sometimes deploying without it at all.
Artificial intelligence is accelerating this shift. Threat actors are using AI-powered tools to generate highly convincing phishing lures and to automate reconnaissance across a wide range of targets. More concerning, AI is enabling polymorphic malware that mutates its appearance across executions while maintaining the same malicious behavior. This makes detection based on static signatures far less effective.
The result is a quieter but more dangerous threat landscape—where attackers may dwell inside systems for extended periods, mapping infrastructure, identifying identity verification systems, and positioning themselves for maximum leverage.
Quantum and the clock on cryptography
While it’s not at full scale yet, quantum computing poses an existential threat to today’s cryptographic infrastructure. Public-key encryption, which secures everything from TLS/SSL certificates to software updates, will eventually be breakable by quantum methods. And that’s not a hypothetical—it’s just a question of timing. For organizations with long-term data sensitivity requirements like healthcare records or financial data, the implications are significant.
Forward-looking attackers know this. Some are already harvesting encrypted data with the assumption that it can be cracked later—a strategy known as “harvest now, decrypt later.” If organizations aren’t thinking about quantum readiness today, they may find that tomorrow’s breakthrough arrives too late to respond.
The main takeaway? Ransomware isn’t just getting more aggressive. It’s getting smarter and more technologically advanced. And that demands a shift in how we think about defense—not as a static perimeter, but as a system that must adapt as fast as the threat.
From prevention to resilience
For years, cybersecurity strategy has centered on prevention: Stop the breach, block the payload, shut down the threat before it starts. But ransomware has exposed the limits of that mindset. Even the best-defended organizations can—and do—get breached. What matters just as much now is what happens next.
Resilience is what allows an organization to take a hit and keep operating. It’s the ability to adapt, recover, and maintain continuity even in the middle of an active incident. And it requires more than just technology—it takes planning, visibility, and infrastructure built for agility.
That means knowing not just where your assets are, but how your systems are connected. It means having clear fallback procedures for business-critical functions. It means building unpredictability into your security controls so attackers can’t rely on repeatable tactics. And it means being able to update cryptographic protocols quickly—especially in response to emerging threats like quantum decryption.
Prevention still matters. But the organizations that recover fastest—and suffer least—are the ones that assume some level of breach is inevitable and build systems that can absorb that impact without breaking.
Digital trust: The backbone of ransomware resilience
One of the most overlooked foundations of ransomware defense is digital trust. More and more, modern ransomware targets the systems that underpin secure operations: certificates, code signing, software updates. If attackers can compromise those, they don’t just disrupt your business—they undermine trust in your brand, your software, and your communications.
That’s why PKI modernization is so critical. Outdated certificate management and rigid cryptographic systems can leave organizations exposed. Manual processes increase the risk of outages. Inflexible encryption makes it harder to pivot to post-quantum algorithms.
Solutions like DigiCert® ONE provide the visibility, automation, and crypto-agility needed to stay ahead of these threats. Whether it’s managing certificates across complex environments or securing the software supply chain, digital trust is no longer a back-office function.
It’s frontline defense.
Build resilience before you need it with DigiCert
Ransomware resilience starts with strengthening the systems attackers increasingly target: identity, software integrity, and cryptographic infrastructure.
DigiCert ONE delivers the visibility, automation, and crypto-agility organizations need to manage certificates at scale, protect software updates, and adapt quickly to emerging threats—including the long-term implications of quantum computing.
Explore DigiCert ONE to see how our AI-powered platform can strengthen your ransomware resilience strategy—today and in the post-quantum future.