-
Platform
Back
DigiCert ONE Integrations
-
Solutions
Back
-
Buy
Back
Signing Certificates
Everything you need to secure your site.
- Company
-
Resources
Back
-
Support
Back
Resources
Contact Support- Americas
- 1.866.893.6565 (Toll-Free U.S. and Canada)
- 1.801.770.1701 (Sales)
- 1.801.701.9601 (Spanish)
- 1.800.579.2848 (Enterprise only)
- 1.801.769.0749 (Enterprise only)
- Europe, Middle East Africa
- +44.203.788.7741
- Asia Pacific, Japan
- 61.3.9674.5500
- Americas
-
Language
- Contact us
DIGICERT CERTCENTRAL®
Best in Class
Public Trust
Easily request, renew, and manage certificates from the most trusted public Certificate Authority in the world.
The DigiCert® ONE Platform
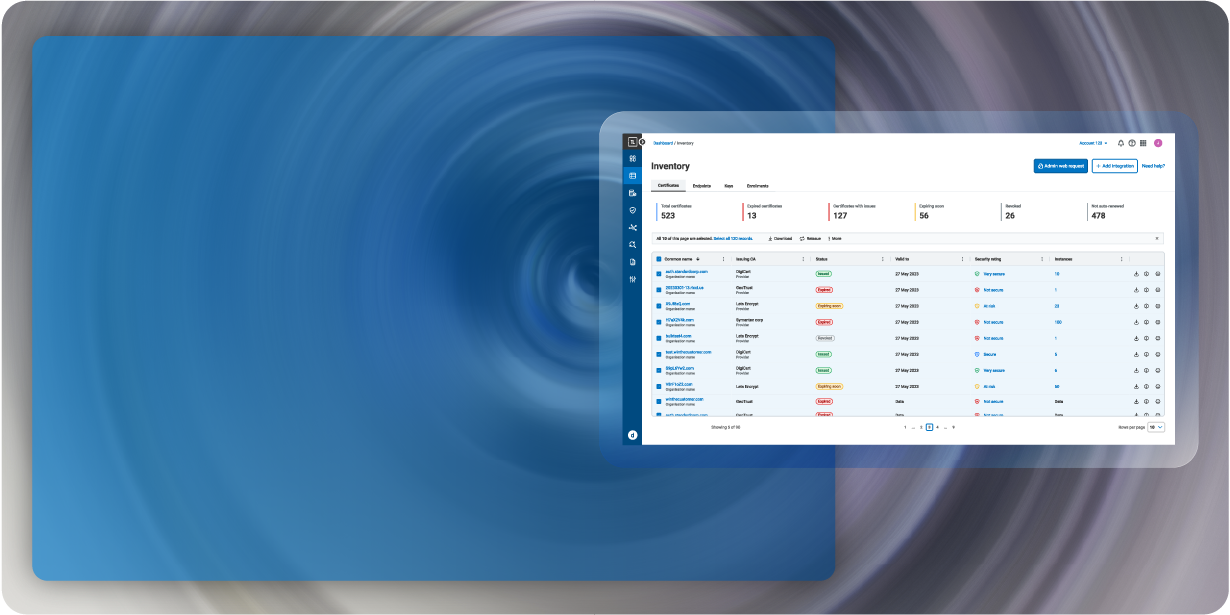
Centralize Public Trust with CertCentral
CertCentral is your foundational solution for establishing and managing public trust across web servers, email, software, and documents.
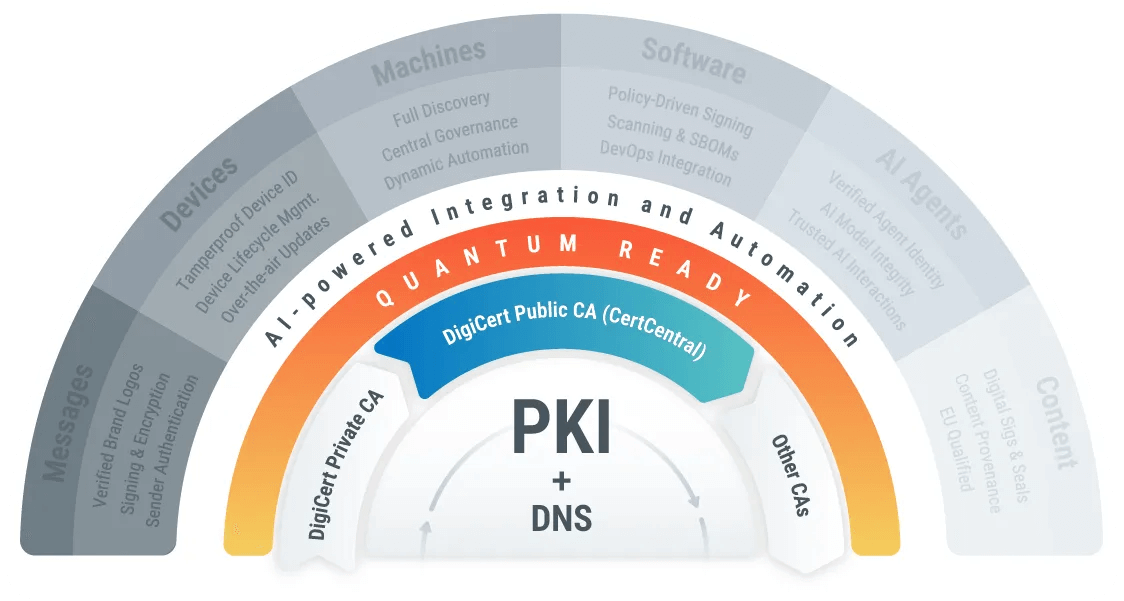
Unrivaled Availability and Scalability for Businesses of All Sizes
Optional heading that can be visually hidden
Fragmented Public Trust
Disparate purchasing and managing certificates for TLS and other Web PKI use cases creates inefficiencies, increases costs due to fragmented procurement, and hampers IT productivity with manual tracking. Ungoverned use of public Certificate Authorities leads to compliance gaps or unexpected distrust incidents, raising the likelihood of outages and security vulnerabilities.
.png)
Use Cases

TLS/SSL CERTIFICATES
Encrypt and authenticate web and other servers on the Internet. DigiCert TLS certificates are available in various configurations to support different use cases and security requirements, including Payment Services Directive 2 (PSD2).
READ MORE

CODE SIGNING
Digitally sign your code to facilitate the authenticity and integrity of software. Optional secure cloud key generation and storage provides turnkey compliance with CA/Browser Forum requirements.
READ MORE

DOCUMENT SIGNING CERTIFICATES
Add digital signatures and seals to documents in a variety of file formats. Through DigiCert CertCentral, you can request document signing certificates to help comply with regulations and standards like PKIoverheid, EU eIDAS and Adobe AATL.
READ MORE

S/MIME CERTIFICATES
Digitally sign and encrypt messages to ensure the integrity and privacy of email communications. Authenticating email senders and messages helps combat email impersonation and compromised content.
READ MORE

DIGICERT MARK CERTIFICATES
Enhance your organization’s email outreach, protect your brand, and make it harder for criminals to impersonate email domains. Includes Verified Mark Certificates (VMC) and Common Mark Certificates.
READ MORE

QUALIFIED AND PKIOVERHEID
DigiCert is a Qualified Trust Service Provider (QTSP), approved by the EU and Dutch governments. These certificates provide the highest level of security and trust, ensuring compliance with stringent European regulations and Dutch government requirements.
READ MORE
The DigiCert CertCentral Difference

Broad Certificate Portfolio
A centralized solution for issuing, monitoring, and renewing over 20 types of publicly trusted digital certificates for enhanced security, compliance, and user experience.

Global Reach. Local Trust.
CertCentral supports over 10 languages. Choose CertCentral Europe for data residency requirements and certificates for compliance with eIDAS, PKIoverheid, and ZertES.

Proven Security and Compliance
CertCentral undergoes over 25 audits annually, ensuring compliance, root ubiquity, and a secure cloud offering that meets industry and regulatory standards.
DigiCert CertCentral
Three things users love about CertCentral
Optional heading that can be visually hidden
Automate DigiCert Certificate Management
Streamline DigiCert certificate management with CertCentral. Automate issuance, renewal, and revocation of DigiCert, GeoTrust, and Thawte TLS/SSL certificates via ACME. For vendor agnostic certificate management and advanced automation, explore DigiCert Trust Lifecycle Manager.
.png)
Optional heading that can be visually hidden
Reporting and Alerts
Comprehensive and customizable reporting enables you to manage certificate expiration, compliance requirements, budgets, and more.
- Create reports in four easy steps
- Choose from a variety of formats
- Customize frequency and delivery
Business Outcomes

Simplified procurement
Consolidating TLS and other public trust purchases improves purchasing power and reduces supplier management.
Operational efficiency
Centralized tracking of public certificates helps IT teams coordinate requests across departments.

Security & compliance
Choosing high assurance certificates with strict personnel and organization validation processes reduces the risk of rogue certificates.

Data residency
CertCentral is available from data centers in Europe, enabling data residency requirements and region-specific trust services.
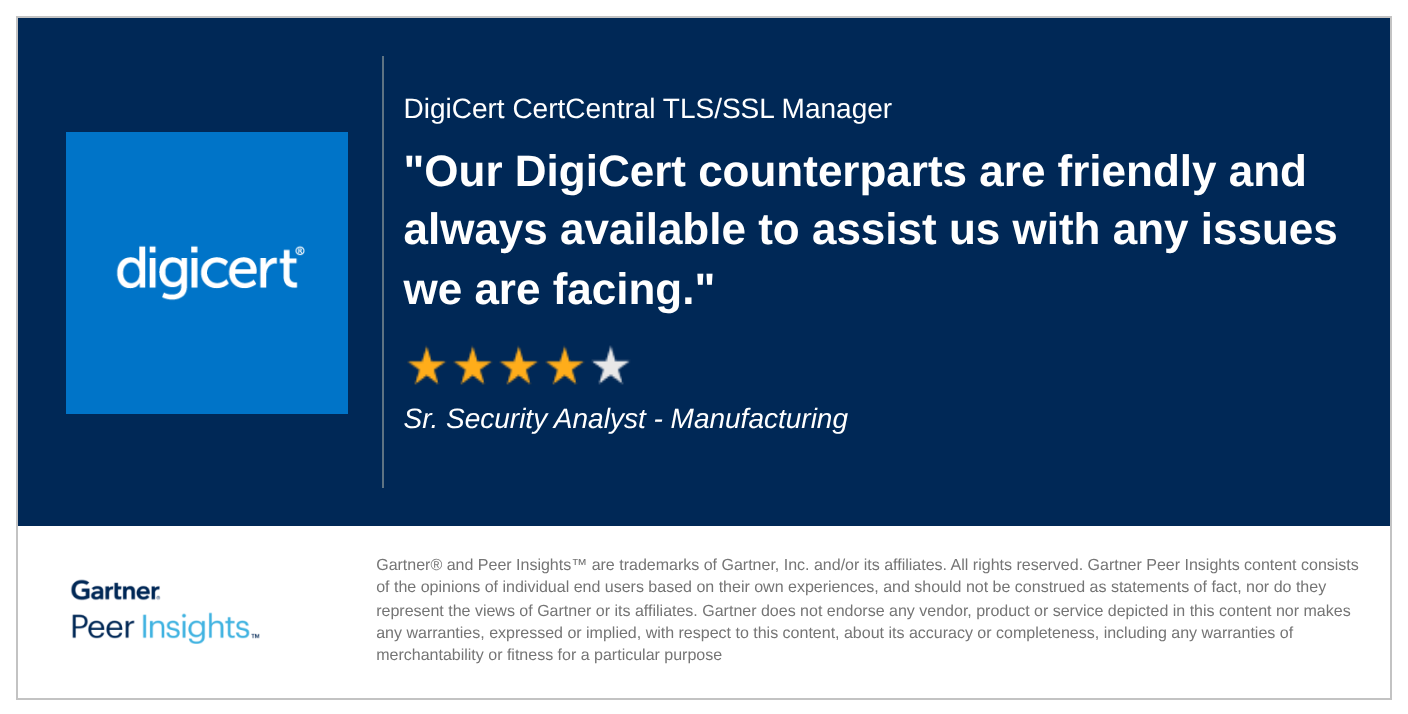
Gartner Peer Insights
Related Resources

DATASHEET
CertCentral Datasheet

DATASHEET
DigiCert Mark Certificates Datasheet

CHECKLIST
TLS Best Practices Checklist
Talk to an Expert About Your Public Trust Needs
-
Company
-
My Account
-
Resources
-
Sites
-
© 2026 DigiCert, Inc. All rights reserved.
Legal Repository Audits & Certifications Terms of Use Privacy Center Accessibility Cookie Settings