-
Platform
Back
DigiCert ONE Integrations
-
Solutions
Back
-
Buy
Back
Signing Certificates
Everything you need to secure your site.
- Company
-
Resources
Back
-
Support
Back
Resources
Contact Support- Americas
- 1.866.893.6565 (Toll-Free U.S. and Canada)
- 1.801.770.1701 (Sales)
- 1.801.701.9601 (Spanish)
- 1.800.579.2848 (Enterprise only)
- 1.801.769.0749 (Enterprise only)
- Europe, Middle East Africa
- +44.203.788.7741
- Asia Pacific, Japan
- 61.3.9674.5500
- Americas
-
Language
- Contact us

DigiCert® Device Trust Manager
Complete IoT
Security Across
the Entire Lifecycle
Secure your IoT devices with Device Trust
Manager for end-to-end lifecycle security,
from manufacturing to retirement.
Optional heading that can be visually hidden
Unique Device. Unique Security.
Devices are different from everything else in the digital world. Different power needs. Different microprocessors and software. Different manufacturing, deployments, uses, and lifespans. Device Trust Manager provides device manufacturers with strong integration and compliance capabilities to meet diverse security needs, providing simple and assured device trust in the ever-evolving IoT landscape.

Trust for Elegant Function
See how TUO Accessories looks at security, design, and function as a singular philosophy behind the devices they make.
WATCH THE VIDEO >
Compliance Without Compromise
As governments around the world look to address IoT security threats, device manufacturers continue to encounter increasing complexity in regulations. Some standards are voluntary, while others are enforceable, like the EU’s Medical Device Regulation (EU MDR) and FDA regulations to proposed certifications. This means manufacturers need to find ways to stay informed and compliant—often in multiple regions with different regulations—without interruptions to development, production, sales, and support.
Leading regulatory standards:
EU MDR | EU Cyber Resilience Act | U.S. Cybertrust Mark | U.S. Food and Drug Administration | CSA Matter
Securing Every Step of the Device Lifecycle
DigiCert Device Trust Manager delivers end-to-end security for IoT devices, embedding advanced protection from inception, ensuring business and regulatory compliance, along with excellent reliability and streamlined operations across the device lifecycle.
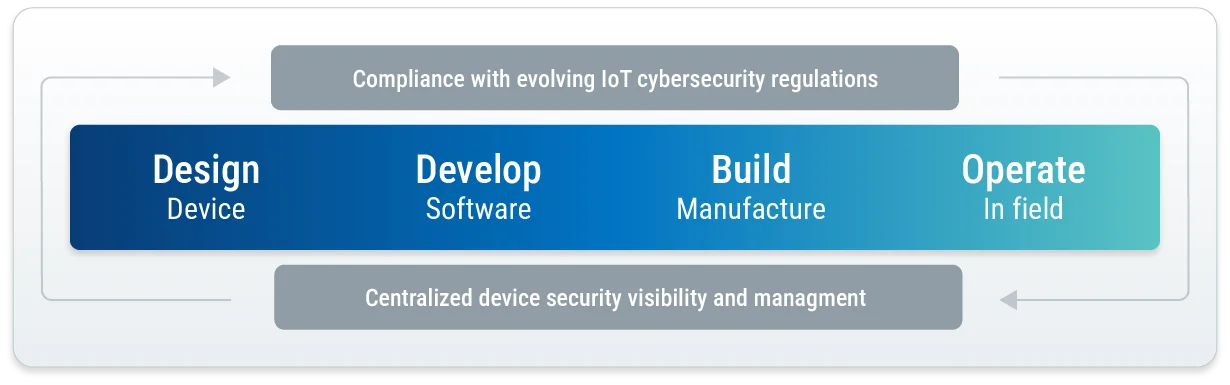
From Concept to Customer: Ensuring End-to-End Security

Design
Prioritize crypto agility. The ability of a system to swiftly shift its cryptographic methods without significant upheaval ensures that as new threats emerge or as quantum computing makes current encryption obsolete, your security infrastructure can transition to more advanced solutions like Post-Quantum Cryptography (PQC). Secure hardware utilizing TPMs and Secure Elements, along with our TrustEdge agent, lay the foundation for a robust security posture, ensuring that devices are built with security as a cornerstone feature.

Develop
Scan your software for threats. Rigorous software vulnerability scanning to catch and mitigate security weaknesses early on. Validated software signing serves as a seal of authenticity and integrity for the software being deployed.

Build
Put trusted roots at the center of your devices.
Hardware-backed identities provide a root of trust for each device, with a secure key and a secure solution for in-factory credential provisioning of IoT devices. This ensures robust certificate injections by third-party manufacturers, providing robust security throughout its lifecycle. This facilitates the trusted, secure provisioning essential for operational integrity.

Operate
Analyze and update at every step. Continuous threat monitoring to swiftly detect and respond to potential security incidents. Deploying secure software updates ensures that devices remain protected against the latest threats, and zero-touch provisioning allows devices to be securely configured and activated with minimal manual intervention.
Elevating Protection With Cutting-Edge Certificate Lifecycle Management
DigiCert Device Trust Manager is an industry-leading solution delivering comprehensive IoT trust to address device manufacturing challenges. With DigiCert Device Trust Manager, you can easily build strong security and updating capabilities into your device, speed time to market, and maintain regulatory compliance.

Identity Assurance
Elevate device integrity with Device Trust Manager’s certificate management, ensuring secure, authenticated device identities effortlessly.

Flexibility in Device Security
Device Trust Manager is a scalable solution that enables secure device management across any environment while enhancing deployment flexibility. It supports batch certificate issuance, secure on-premises issuance via a gateway, and both birth and operational certificate issuance. Utilizing protocols like REST API, SCEP, EST, ACME, and CMPv2, it ensures efficient, secure provisioning and seamless system integration with MQTT.

Identity Injection
Tailored for manufacturability, Device Trust Manager seamlessly integrates with third-party manufacturing to inject device components with secure identities using birth certificates, optimizing production line efficiency.

Matter Compliance for IoT
DigiCert ensures compliance and interoperability with the CSA Matter protocol, a pivotal step forward in integrating and securing smart home ecosystems. Our participation with the Connectivity Standards Alliance in developing the Matter standard exemplifies our dedication to advancing secure, seamless connectivity across smart home devices. By aligning with Matter, DigiCert champions a unified approach to IoT security, offering manufacturers and consumers a framework for interoperability and trust in the expanding ecosystem of connected devices.
SEE HOW DIGICERT WORKS WITH MATTER >

A Foundation for Digital Trust
DigiCert ONE is more than just a platform. It’s a new way of thinking about how you secure and manage everything of value in your organization. From the individual website to the massive enterprise, DigiCert ONE makes security, validation, and identity powerful and easy. No matter the size or use, DigiCert ONE delivers control and simplicity for the highest level of assurance.
Take a look at our other DigiCert ONE managers
DIGICERT® CERTCENTRAL TLS MANAGER
DIGICERT® TRUST LIFECYCLE MANAGER
DIGICERT® SOFTWARE TRUST MANAGER
DIGICERT® DOCUMENT TRUST MANAGER
DIGICERT® DNS TRUST MANAGER
Already using DigiCert ONE? Log in now.
Related Resources

EBOOK
Securing the future of smart technology

DOCUMENTATION
Device Trust Manager

BLOG
Smart security for smart medical devices
Partnerships Work to Deliver Excellence
Building IoT solutions is a "team sport" and using the right partners can accelerate time to market. We have partnered with leading companies who can help you design, build, secure and operate your connected product solution. Learn More >







Talk to an Expert to Learn How DigiCert
Solutions Can Help You Deliver Digital Trust
-
Company
-
My Account
-
Resources
-
Sites
-
© 2026 DigiCert, Inc. All rights reserved.
Legal Repository Audits & Certifications Terms of Use Privacy Center Accessibility Cookie Settings

