-
Platform
Back
DigiCert ONE Integrations
-
Solutions
Back
-
Buy
Back
Signing Certificates
Everything you need to secure your site.
- Company
-
Resources
Back
-
Support
Back
Resources
Contact Support- Americas
- 1.866.893.6565 (Toll-Free U.S. and Canada)
- 1.801.770.1701 (Sales)
- 1.801.701.9601 (Spanish)
- 1.800.579.2848 (Enterprise only)
- 1.801.769.0749 (Enterprise only)
- Europe, Middle East Africa
- +44.203.788.7741
- Asia Pacific, Japan
- 61.3.9674.5500
- Americas
-
Language
- Contact us

Complimentary research
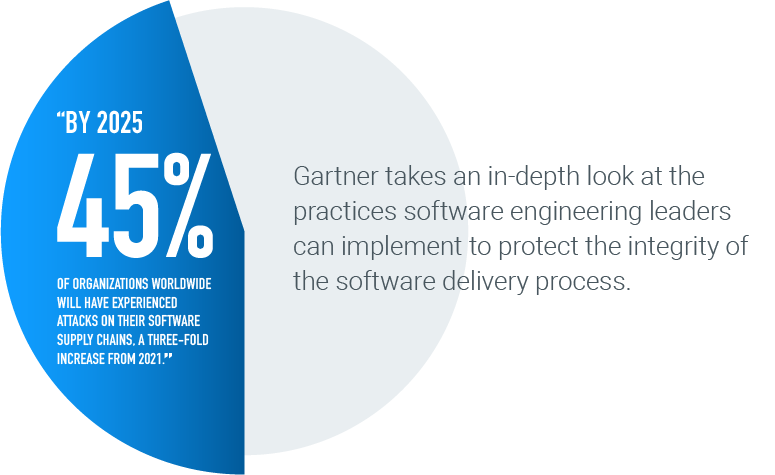
How Software Engineering Leaders Can Mitigate Software Supply Chain Security Risks
Explore potential software supply chain security risks and the strategies software engineering teams can use to counter them.
Optional heading that can be visually hidden

Read the Report to Learn About:

The methods attackers use to compromise continuous integration/continuous delivery (CI/CD) systems and inject malware into legitimate software

How to protect the integrity of internal and external source code

How to prevent cloned repositories from becoming a treasure trove for attackers looking to steal credentials, API keys or secrets

How to manage the risks associated with the use of third-party software

How to harden the software development and delivery pipeline

How Software Engineering Leaders Can Mitigate Software Supply Chain Security Risks. By Manjunath Bhat, Dale Gardner, Mark Horvath. Published 15 July 2021. Refreshed 22 November 2022.
GARTNER is a registered trademark and service mark of Gartner, Inc., and/or its affiliates and is used herein with permission. All rights reserved. Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
-
Company
-
My Account
-
Resources
-
Sites
-
© 2026 DigiCert, Inc. All rights reserved.
Legal Repository Audits & Certifications Terms of Use Privacy Center Accessibility Cookie Settings

