
DigiCert® TLS/SSL Certificates Overview
A Lock, Two Keys and Strong Identity
Establishing trust from the back end of
eCommerce websites to delivery at your
front door. That's digital trust for the real world.
What Are TLS/SSL Certificates?
Transport Layer Security (TLS) certificates—most commonly known as SSL, or digital certificates—are the foundation of a safe and secure internet. TLS/SSL certificates secure internet connections by encrypting data sent between your browser, the website you’re visiting, and the website server. They ensure that data is transmitted privately and without modifications, loss or theft.
Select Your Cert

TLS is the successor technology to Secure Sockets Layer (SSL) which was replaced in 2015 after it was compromised by several vulnerabilities. Most people use the common term SSL because it's more widely known. However, when you buy a TLS/SSL certificate from DigiCert, you get the latest and highest level of TLS encryption certificate on the market.
Why Do Sites Need to Use TLS/SSL Certificates?
TLS/SSL certificates are the standard by all major web browsers to ensure a safer internet experience for users. Websites secured by TLS/SSL certificates are more trusted by internet users because they encrypt and protect private information transferred to and from their website. They also represent, or certify, your website’s brand identity. In that sense, TLS/SSL certificates are both an identity protection measure for online brands, and a security measure for companies transmitting private data online.
Optional heading that can be visually hidden
TLS/SSL Certificates and Digital Trust
Give customers a clearer picture of who you are.
Jane Doe is an anonymous, unidentifiable internet user whose actions can’t be tracked. Would you trust her with your personal information?
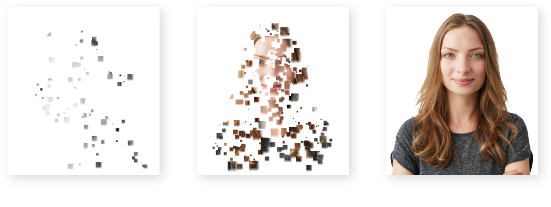
High-Assurance EV & OV Certificates Protect Your Brand
EV TLS/SSL certificates protect businesses and brands because they certify that website owners are the authentic owners of their website.
Before you can obtain an EV certificate, users must demonstrate that they have legal rights to represent their business organization, web domain, physical address, and business entity, among 14 other criteria.
OV certificates are secondary to EV because they require similar methods of authentication, including verifying the web domain, and affiliated business organization, such as Inc., Corp, LLC, etc. However, OV certificates only require 9 methods of validation compared to the 14 methods required for EV.
When Personal Information is on the Line, Only the Highest-level Certificates Will Do
EV & OV certificates are used by 81% of businesses in the Global 2000, 89% of Fortune 500 companies and 97 of the 100 largest banks worldwide. The list of high-assurance EV & OV TLS/SSL certificate users includes IT companies, utilities companies, retail, real estate, insurance, automotive, telecom and hospital and healthcare companies.
TLS/SSL Certificates Improve SEO
It’s no secret that a secure internet is a better internet. That’s why most major browsers require TLS/SSL certificates—and boost the results of websites that are secured by digital certificates. This includes all major search engines and all browser types.
Compare TLS/SSL Certificate Uses
Uses
Informational sites & blogs
Websites that don't collect payments or sensitive information need HTTPS to keep user activity private-even blogs.
Login panels & forms
TLS/SSL encrypts and protects usernames and passwords, as well as forms used to submit personal information, documents or images.
Checkout pages
Customers are more likely to complete a purchase if they know your checkout area (and the credit card info they share) is secure.
Recommmended TLS/SSL Certificate type
OV (Organization Validated) TLS/SSL certificates - The second highest level of authenticity and next most rigorous organization checks.
OV (Organization Validated) TLS/SSL certificates - The second highest level of authenticity and most-rigorous organization checks.
EV (Extended Validation) TLS/SSL Certificates - The highest level of authenticity and most-rigorous identity checks.
DigiCert Products
FAQ
How do TLS/SSL certificates work?
TLS/SSL certificates establish an encrypted connection between a website/server and a browser with what’s known as an “SSL handshake.” For visitors to your website, the process is invisible—and instantaneous.
What is digital trust?
Digital trust is a modern combination of encryption, security and identity solutions designed to extend protection across every virtual interaction and build a bridge of trust between the digital and physical worlds. Essentially it's the unification of TLS/SSL, IoT and PKI security through a centrally managed platform.
Do TLS/SSL certificates work on all devices, systems and versions?
Yes DigiCert TLS/SSL certificates are issued under one of the longest-lived and most widely supported roots in the industry. DigiCert TLS/SSL certificates deliver the highest root ubiquity on 99.9% of web browsers, major operating systems and mobile devices. If you have questions about the compatibility of older devices, please contact our support team.
Does my website need a TLS/SSL certificate?
Yes, most websites that conduct business on the internet require a digital TLS/SSL certificate to encrypt and secure private data that is transmitted. TLS/SSL certificates protect your business’ and your customers private information. In addition, without a certificate most major browsers will display a “Not Secure” message in the address bar. Having an unsecure website could prevent customers from completing purchases or doing business with your company. If you want to signal the highest level of security and brand authenticity to customers, we recommend using an EV or OV certificate.
Why is my website showing a “Not Secure” message in the browser address bar?
Any website without a secure TLS/SSL certificate will show a “Not Secure” message in the browser address bar. The only way to fix a “Not Secure” message on your website is by installing a TLS/SSL certificate. You can do that by purchasing a certificate from DigiCert and following the installation steps in CertCentral.

