-
Platform
Back
DigiCert ONE Integrations
-
Solutions
Back
-
Buy
Back
Signing Certificates
Everything you need to secure your site.
- Company
-
Resources
Back
-
Support
Back
Resources
Contact Support- Americas
- 1.866.893.6565 (Toll-Free U.S. and Canada)
- 1.801.770.1701 (Sales)
- 1.801.701.9601 (Spanish)
- 1.800.579.2848 (Enterprise only)
- 1.801.769.0749 (Enterprise only)
- Europe, Middle East Africa
- +44.203.788.7741
- Asia Pacific, Japan
- 61.3.9674.5500
- Americas
-
Language
- Contact us
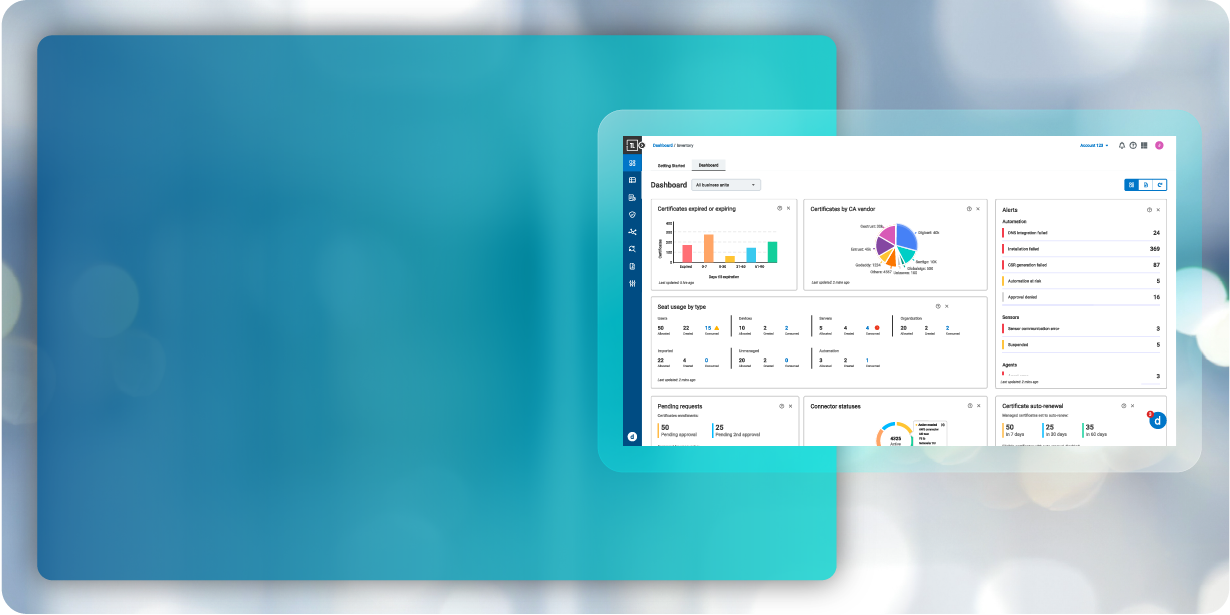
DIGICERT® TRUST LIFECYCLE MANAGER
Full Visibility,
Zero Certificate Disruptions
Strong security starts with strong PKI.
Gain control, stay compliant, and eliminate certificate disruptions.
The DigiCert® ONE Platform
Gain visibility, eliminate outages and reduce costs with enterprise PKI and Certificate Management.
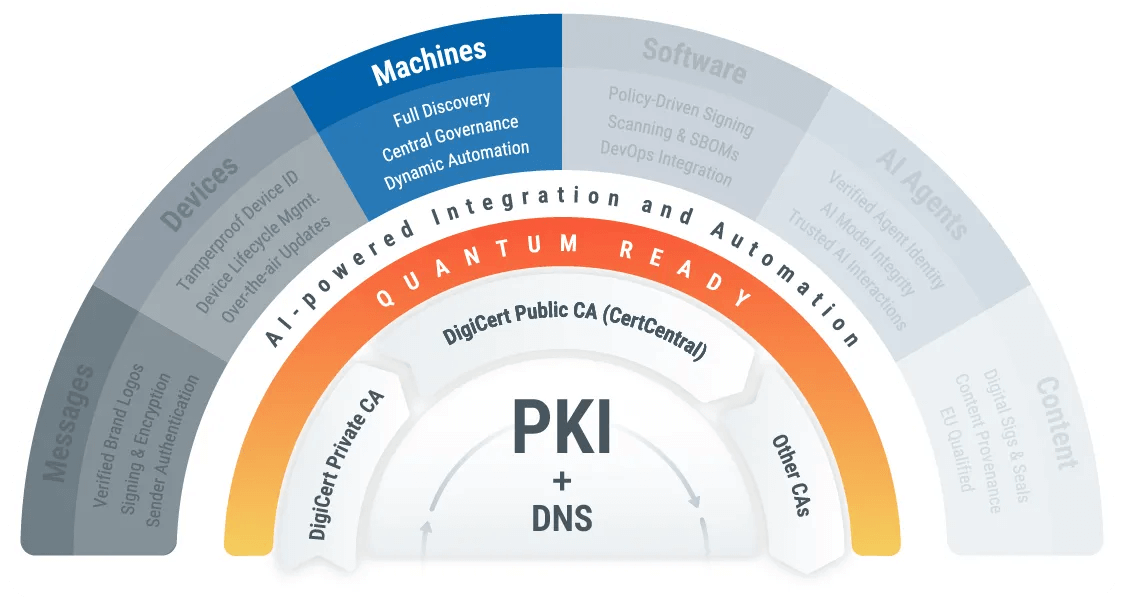
Optional heading that can be visually hidden
The Pressing Need for
Crypto-Agility
Traditional PKI lifecycle management tools lack automation, visibility, and flexibility, forcing IT teams to react to problems instead of preventing them.
The answer? A unified, automated PKI solution for full control over public and private certificates—no matter which authority they were issued by.

Use Cases

SERVERS & INFRASTRUCTURE
Secure, automated, CA-agnostic certificate management with agent/agentless support, multi-forest Active Directory compatibility, and network device integration to enhance security, achieve compliance, and prevent outages.

USERS & DEVICES
Enable secure user and device authentication with UEM integration, Zero Trust VPN/WiFi access, and smart card-based secure email for seamless, policy-driven security enforcement.

CLOUD WORKLOADS
Ensure secure container communications across hybrid and multi-cloud environments with secret management vaults and Infrastructure-as-Code (IaC) integrations for seamless certificate management and workload protection.

PRIVATE (INTERNAL) PKI
Simplify PKI with a scalable, cloud-based managed PKI that enables seamless integration, quantum-ready security, centralized governance, and reduced operational costs—no specialized expertise required.

Years of PKI Excellence
For 25 years, DigiCert has led PKI innovation, providing scalable, trusted certificate management solutions for enterprises, governments, and critical infrastructure.

Key Signings Per Year
DigiCert performs 3100+ key signings annually, ensuring secure, trusted PKI operations for enterprises, governments, and global organizations across diverse industries.

Public & Private Roots
DigiCert maintains 2600+ global private and public roots, enabling secure, scalable PKI for enterprises, governments, and global organizations across diverse industries.
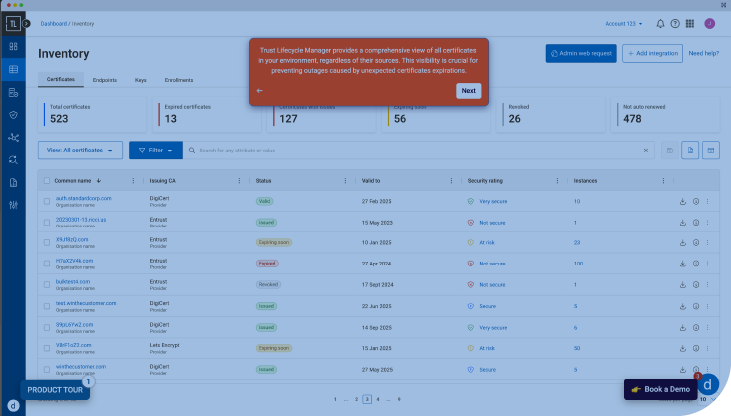
Alleviate Certificate Management Challenges
Stop outages and take control of your certificate management
Optional heading that can be visually hidden
Simplified, Automated and Secure Certificate Management
Gain complete visibility and control over certificates across hybrid environments, automate lifecycle processes to prevent outages, and enforce compliance with industry regulations—seamlessly integrating PKI into DevOps workflows for scalable, secure deployments.

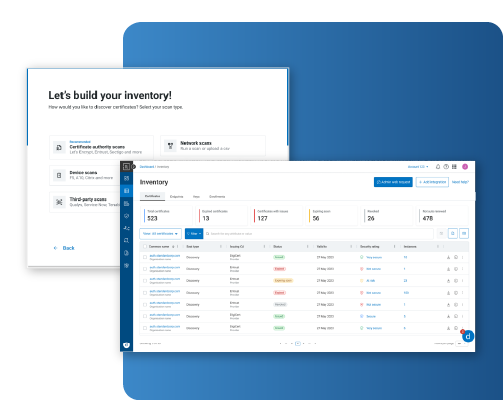
Know your PKI with Full Discovery
Discover and build a full certificate inventory using multiple techniques.
- Certificate Authority Agnostic
Import from any CA/PKI system including public and private. - Networks and Cloud Visibility
Scan the entire network and cloud for everything PKI. - Structuring the Unstructured
Get auto tagging.
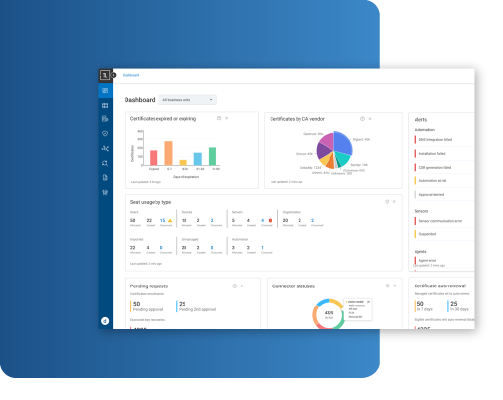
Mitigate Risks With Central Governance
Enforce Enterprise PKI Policies while Enabling Decentralized Operations
- Enforce PKI Policies
Eliminate weak keys, deprecated algorithms, and unauthorized CAs - Simplify Audits and Compliance
Meet PKI compliance controls, reduce cost, and time of audits - Decentralize Operations
Enable self-service and role-based admin with centralized governance.
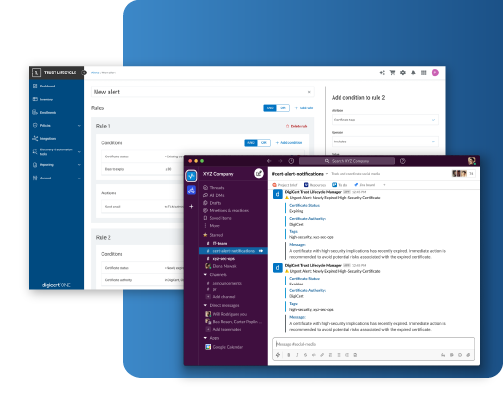
Prevent Outages With Timely Alerts
Know Asset Owners and Proactively Notify them of Expiring Certificates
- Assigned Asset Owners
Never miss a certificate renewal that impacts a critical service - Dynamic Rule Engine
Prioritize alerts based on business impact, e.g. expiration and criticality - Flexible Alert Mechanisms
Alert the right person on the right channel, e.g. email, text, Slack

Drive Resilience With Dynamic Automation
Prevent Critical Service Outages Caused by PKI and reduce staff costs.
- Seamless Integrations
Extensive agent and agentless options for enterprise systems
Go to Integrations Directory >> - Protocols and API Support
Seamless support for ACME, EST, SCEP and CMPv2 architecture - Self-Service Portal
On-demand certificate issuance, renewal, and management
Business Outcomes

Mitigate Risks
Ensure consistency and compliance across your certificate landscape with centralized governance.

Reduce Costs
Automate renewals so you can rest easy knowing you’re always protected from costly outages.

Prevent Outages
Get alerts about certificate validity mandates, sudden revocations, and distrust scenarios.
Meet Compliance Mandates
Streamline PKI management to prevent compliance failures, security threats, and downtime. Achieve full visibility into your PKI environment, ensuring regulatory adherence and uninterrupted operations.
Optional heading that can be visually hidden
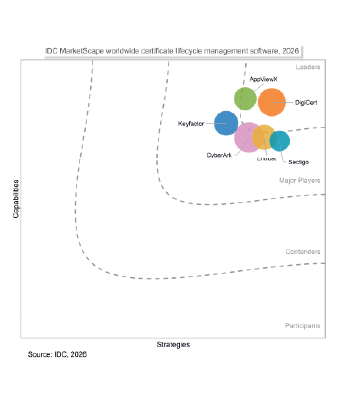
DigiCert Named a Leader in the 2026 IDC MarketScape
for CLM
Read the IDC MarketScape excerpt to see DigiCert's complete evaluation and understand why we were recognized as a Leader for Certificate Lifecycle Management.
Major Entertainment Company Secures PKI Following Breach
After a $100M+ cyberattack, a major entertainment company turned to DigiCert for rapid certificate automation, eliminating rogue CAs and protecting 500K+ machines against outages and future threats.
Optional heading that can be visually hidden
“Few vendors stand up & shine when it matters. DigiCert showed true Customer Obsession and flew in the same day."
-Vice President, Cyber Defense

Related Resources

CASE STUDY
Zscaler’s journey to faster, more secure certificate management

WHITE PAPER
Modernize Your PKI for Security,
Efficiency and Agility

EBOOK
PQC for Dummies

EBOOK
TLM Use Case eBook
Talk to an Expert or Schedule a
Trust Lifecycle Manager Demo Today
-
Company
-
My Account
-
Resources
-
Sites
-
© 2026 DigiCert, Inc. All rights reserved.
Legal Repository Audits & Certifications Terms of Use Privacy Center Accessibility Cookie Settings

