
Digital Trust
What is PKI?
From the bottom of the ocean to the edge of space, PKI establishes trust. At DigiCert, we help you manage and extend it across entire ecosystems. That’s digital trust for the real world.
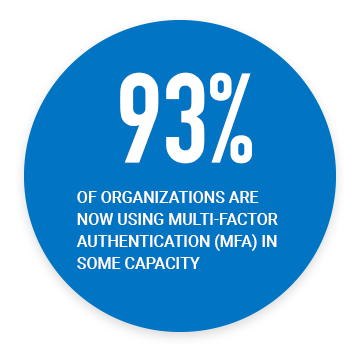
Passwords No Longer Cut It
Your information is as essential as any of your business assets. Adding extra layers of security to your most valuable systems and data is no longer just an option—it’s a necessity. With PKI, you can employ advanced authentication and encryption methods to mitigate risks to your network.
What is PKI?
Public Key Infrastructure (PKI) is a system of processes, technologies, and policies that allows you to encrypt and sign data. You can issue digital certificates that authenticate the identity of users, devices, or services. These certificates create a secure connection for both public web pages and private systems—such as your virtual private network (VPN), internal Wi-Fi, wiki pages, and other services that support MFA. Have questions?
Optional heading that can be visually hidden
What is Private PKI?
Private PKI allows you to issue your own private SSL certificates off a unique intermediate root often maintained by a publicly trusted CA. This allows you to tailor certificates around unique needs and deploy on-demand certificates for internal purposes.

Common PKI Use Cases
PKI Isn’t Just for Web Security
Despite common misconceptions, PKI is a perfect match for the exploding IoT sector, providing critical authentication measures.
Related Resources

WEBPAGE
PKI Ebook - Where You Need Trust, You Need PKI

White Paper
5 Steps to building a Scalable PKI

Blog
How to build a PKI that Scales Interview Series
Talk to an Expert to Learn How Digicert Solutions
Can Help You Deliver Digital Trust
FAQS
What is PKI?
Public Key Infrastructure (PKI) is a system of processes, technologies, and policies that allows you to encrypt and/or sign data. With PKI, you can issue digital certificates that authenticate the identity of users, devices, or services. These certificates work for both public web pages and private internal services (e.g., to authenticate devices connecting with your VPN, Wiki, Wi-Fi, etc.)
Why should my organization use PKI?
With Public Key Infrastructure (PKI), you can significantly increase the security level of your network. Three key benefits make this possible:
- Authentication: Validate identities to ensure only authorized users and devices have access to a server.
- Encryption: Use a certificate to create an encrypted session, so information can be transmitted privately.
- Data Integrity: Ensure any messages or data transferred to and from devices and servers are not altered.
How is PKI used?
Common use cases for PKI include, but are not limited to:
- Securing web pages
- Encrypting files
- Authenticating and encrypting email messages using S/MIME
- Authenticating nodes connecting to a wireless network
- Authenticating connections to your VPN
- Authenticating connections to sites and services containing corporate data using TLS mutual authentication
What’s end-to-end encryption?
End-to-end encryption is when a message is encrypted at your device, and the decryption is done at the recipient’s device. This means that no third party can intercept your sensitive data.
What is a CA?
A Certificate Authority (CA) is a trusted third party that verifies the identity of an organization applying for a digital certificate. After verifying the organization’s identity, the CA issues a certificate and binds the organization’s identity to a public key. A digital certificate can be trusted because it is chained to the CAs root certificate.
What is a digital certificate?
A digital certificate vouches for the holder’s identity. Like a driver’s license, the certificate has been issued by a trusted third party, cannot be forged, and contains identifying information.
What are public and private keys, and how are they related?
Public and private keys are used to encrypt and decrypt information. Only the private key can decrypt information encrypted by the public key. This key pair is known as asymmetric cryptography (because the encryption is done using non-identical keys). The two keys are mathematically related, but it’s impossible to determine one key using the other.
What are public and private roots?
A root certificate provides the signature when binding an identity to the public key. This is how you identify whether a certificate is valid, and whether you should trust it.
Does DigiCert offer solutions for both public and private PKI?
The short answer is, yes. DigiCert offers solutions for both public and private PKI, along with a platform and RESTful API, which allow you to automate certificate management and customize PKI workflows. You may have only worked with a commercial CA to purchase public SSL certificates. With this as your only reference point, you might assume private certificates have similar costs as public certificates—this isn’t the case. Issuing a private digital certificate with DigiCert is a fraction of the cost of a public certificate.
Security engineers and administrators sometimes mistakenly think a hosted private PKI will limit them to certain certificate profiles. They think they’ll only have access to certificate profiles that are approved by the CA/Browser Forum. However, DigiCert can provide you with any certificate profile you need. These certificate profiles don’t have to be SSL/TLS certificate profiles—they don’t even have to be X.509.
What’s MPKI?
Managed PKI (MPKI) is a solution provided by a CA that allows you to begin automating certificate processes and customizing PKI workflows. Once your organization gets to the point that it requires a high volume of certificates, you’ll benefit from an MPKI solution that simplifies certificate management.
Should we set up an internal CA (build) or use a hosted CA (buy)?
You can secure your internal services (e.g., VPN, WiFi, Wiki, etc.) using an internal CA. Organizations commonly do this using Microsoft CA. However, building and maintaining an internal CA can be expensive and time-consuming. You’ll want to carefully consider the costs of each before deciding. Many CAs provide hosted solutions that can save you from some of the hardware, software, and personnel costs involved in building an internal PKI.
What is a Certificate Policy?
A Certificate Policy (CP) is a document created to identify the different actors of a PKI and their roles and duties. The CP specifies practices like how certificates can be used, how certificate names are to be chosen, how keys are to be generated, and much more. The associated CP is typically specified in a field of the X.509 certificate. For in-depth information on CP, see the most up-to-date reference document (RFC 3647): https://tools.ietf.org/html/rfc3647
What is key storage and how should we handle it?
Key storage, often referred to as key archival, is securely storing the private key in case it’s lost. To meet FIPS compliance, and ensure the highest level of security, we suggest storing your keys using a Hardware Security Module (HSM).
What is an HSM?
An HSM is a cryptographic hardware-based option for secure key storage. Typically, HSMs are physically located on-premises, and require internal resources to maintain. This can be cost intensive, but less expensive options do exist. For example, the Microsoft Azure Key Vault provides secure storage of keys in Microsoft’s cloud HSM. If you’re a smaller organization, or don’t have the resources to purchase and maintain your own HSM, Microsoft Azure Key Vault is a viable solution. Some public CAs, including DigiCert, offer integrations with Microsoft Azure.
How do I get started with building a PKI?
To get started, you’ll need to evaluate your environment by considering your needs and the technology you’re working with. We suggest these five steps to get started:
- Identify your non-negotiable network security risks
- Pinpoint the network security risks PKI can mitigate
- Develop the right mix of public and private PKI
- Decide whether to build (internal CA) or buy (hosted CA)
- Determine how to automate delivery of certificates to devices
If you need help, contact one of our PKI architects by sending an email to enterprise@digicert.com.

