
The internet has transformed the way we live, shop, and connect. But it’s also opened the door to cybercriminals looking to exploit our trust. Fake websites are everywhere, and they look just like the legitimate ones you know and trust.
From phishing scams and counterfeit eCommerce stores to fake login pages that harvest your credentials, these sites are getting more sophisticated by the day. The stakes couldn’t be higher, especially as more of our personal and professional lives move online.
Knowing how to spot scam websites isn’t just a skill; it's a necessity. Whether you’re shopping for a holiday gift or logging into your bank account, here’s how to verify a website to save yourself time, money, and a lot of stress.
1. Check the URL
One of the simplest ways to spot a fake website is by carefully examining the URL. Fraudsters often tweak the spelling of familiar domain names in subtle ways, hoping you won’t notice. They might swap a letter for a similar-looking character, like replacing the "o" in amazon.com with a zero to create amaz0n.com. Or they could change the domain extension entirely—switching from .com to .org, .net, or another less familiar extension so the URL reads amazon.org or amazon-shop.net.
These small changes are easy to miss, especially if you’re in a rush. That’s why it’s important to take a moment to verify the URL before entering any personal information or making a purchase. Hover over links in emails or ads to see the full URL before clicking, and always type trusted URLs directly into your browser to avoid being misled by what pops up in search results. When in doubt, look for inconsistencies or anything that feels off—your attention to detail could save you from falling victim to a scam.
2. Check for a site seal

A site seal is a visual indicator that a website has undergone verification, signaling to users that the site is authentic and secure. Trusted seals often belong to well-known certificate authorities (CAs) like DigiCert, and they're interactive—when you click on the seal, you'll see additional details about the website’s security measures and how it was verified. This might include the organization’s name, the type of security certificate it uses, and the issuing authority.
If a site seal doesn’t respond when clicked or redirects to an unrelated or suspicious page, consider it a red flag. Fraudsters often copy trusted site seals and paste them onto fake websites to create a false sense of legitimacy. If you encounter a seal that seems questionable, take extra precautions by cross-checking the URL and other security features of the site to ensure the website owner is who they say they are.
3. Check the site's security information
Websites use TLS/SSL certificates to encrypt the data exchanged between your device and the site to protect it from interception by attackers. Three types of TLS certificates are used to encrypt data:
- Domain validation (DV) certificates: Confirms domain ownership but doesn’t verify organizational details, making it unsuitable for commercial use.
- Organization validation (OV) certificates: Authenticates the organization through business registration databases; ideal for commercial or public websites.
- Extended validation (EV) certificates: Provides the highest level of authentication with rigorous checks, including business verification and direct contact. Trusted by top organizations, EV certificates assure users of the website’s legitimacy and ownership.
Fraudsters typically use DV certificates—the low-level TLS certificates that some CAs offer for free—because they only require proof that the fraudster owns the site.
Where to find a site’s security status
When you visit a website, your browser provides visual cues about the site’s certificate and connection status. In Chrome (and many other browsers), this is indicated by the small icon to the left of the URL in the address bar, often referred to as the "site information icon," which you can click to get more information about the site’s security.
Here’s a quick guide to the different security indicators you can look for to visually verify that a TLS certificate is keeping your data safe.
- A padlock icon means the site is using Hypertext Transfer Protocol Secure (HTTPS), ensuring a secure connection. Click on the padlock to see details about the certificate and the organization that issued it.
- An info icon (a letter "i" inside a circle) means the site doesn’t fully meet modern security standards. The site might still use HTTPS, but elements like images or scripts may not be encrypted. If you see the info icon, don’t enter sensitive information until you’ve confirmed the site is safe.
- A triangle with an exclamation mark is a warning that the connection isn’t secure. The site uses HTTP instead of HTTPS, meaning your data is transmitted in plain text and open to interception. If you see this icon, don’t enter your password, credit card, or other personal details.
- A "Not Secure” label (sometimes displayed as a red or broken padlock) is an explicit warning that the site’s security is highly compromised and unsafe to navigate.
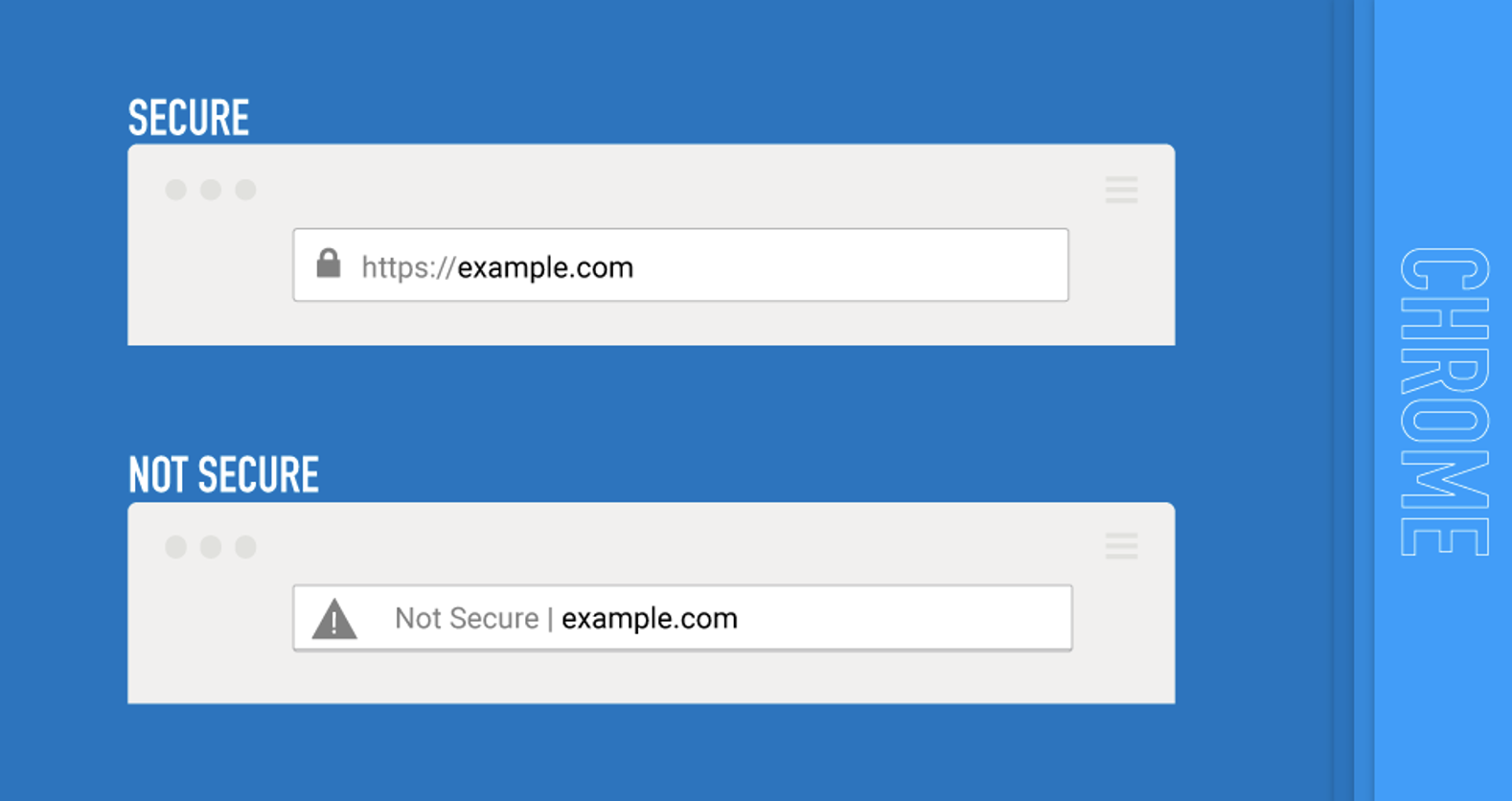
While the padlock is a helpful starting point, keep in mind that it doesn’t guarantee the legitimacy of the site—only that the connection is encrypted. You can look beyond the lock by clicking on it once to reveal more information.
Always pair this check with other verification steps, like looking for proper domain spelling, examining site seals, and ensuring you’re on the correct URL. Little habits like these will greatly reduce your risk of falling victim to scams.
4. Use a website checker
When in doubt, use a website checker to verify if a website is secure. Tools like Google Safe Browsing provide detailed insights into a site’s security status. All you have to do is drop the URL into the status checker to see if it’s safe or vulnerable to threats like malware, phishing, or weak encryption.
5. Look for other trust indicators
A website’s technical information isn’t the only way to tell if it’s a safe place to shop. Here are some other markers most legitimate companies have on their websites:
- A privacy policy
- A return policy
- Contact information like a business phone number and address
- Correct spelling and grammar
It’s also wise to look at online reviews. And remember that if a deal seems too good to be true, it probably is.
6. When in doubt, don’t fill it out
This should go without saying, but we’ll say it anyway: If you discover that a site you’ve landed on is fraudulent, don’t provide sensitive information like financial details, verification codes, a login and password, or your name and contact information.
If you land on a fake website, report it to Google Safe Browsing to help keep other shoppers safe.
The latest developments in digital trust
Want to learn more about topics like TLS/SSL, smart seals, and cybersecurity? Subscribe to the DigiCert blog to ensure you never miss a story.




